Ransomware: What are the legal implications of your business getting hit?

How do you react in accordance to the law when you're hit with ransomware?
Once it was mainly just a problem for unlucky individuals, but now ransomware is becoming a pressing concern for the enterprise, as cybercriminals increasingly target corporate networks with the file-encrypting malware.
The thinking behind hitting businesses is relatively simple: while business networks may, in theory, be more difficult to penetrate with ransomware-dropping techniques such as phishing, the pay-off can be much larger.
Security
Cybercriminals targeting corporate networks is hardly a new phenomenon. However, there are often legal implications to be taken into account when they're hit, and the victim organisation can potentially be fined or taken to court if their security setup is deemed to be outright negligent.
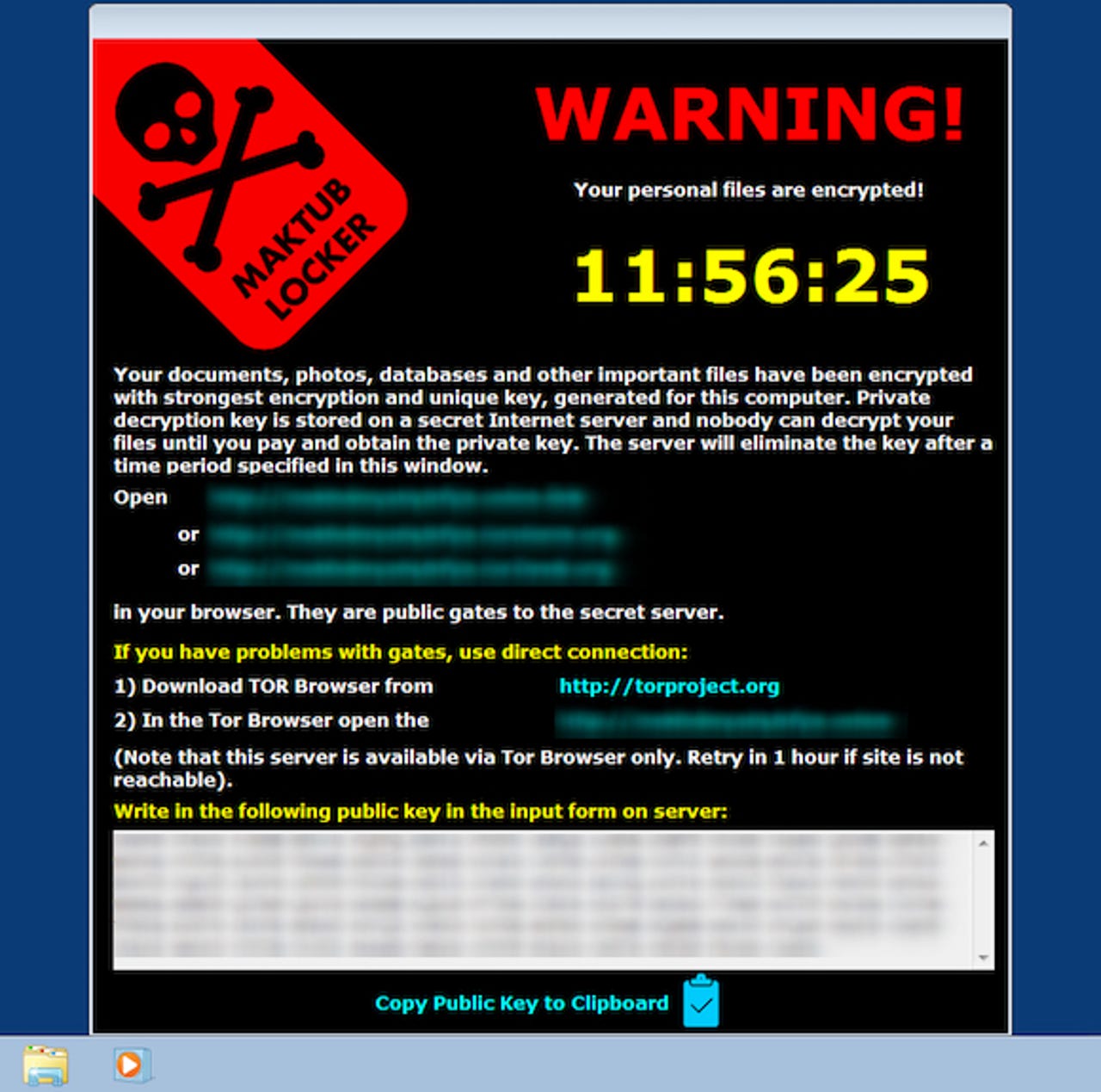
In many of these incidents, the evidence that there's been a breach is patently obvious: data is often put up for sale or even just dumped online. But what are the legal implications of an enterprise network being infected with ransomware?
Emma Wright, commercial technology partner at law firm Kemp Little, says that even if encrypted data isn't outright stolen or published, the information has still been subject to unauthorised access by individuals outside the company.
Highlighting that, despite the fact the data may not have leaked, someone who doesn't have consent to view the information has accessed it nonetheless, Wright told an Intel Security roundtable: "Even the fact a third-party has accessed that data is a breach of data protection law anyway. Because it's been released to a third party, it's a breach of the Data Protection Act, but it's not public."
While the US Department of Health and Human Services recently issued guidance on ransomware, suggesting that this type of attack will be considered a data breach, for Intel Security's EMEA CTO Raj Samani, while a ransomware infection is still very much a problem for the business which falls victim to it, he argued it doesn't necessarily constitute a breach because "the data hasn't technically left the organisation".
"I get the logic but, for me, a breach for me is where data is taken away from the organisation. Yes, [cybercriminals] had access, but nobody sat and read that data, what they did is they just performed an encryption function against it," he said.
However, for Kemp Little's Wright, a businesses succumbing to a successful ransomware attack very much constitutes a data breach in accordance with the Data Protection Act, which puts it in the context of control of data.
If ransomware gets put onto a PC, it's no longer under the sole command of a business: "If you're a data controller, you've lost control because you no longer control that data or where that data could be shown," she said.
So if a ransomware infection is classed as a data breach, do organisations need to adhere to the European Union's upcoming General Data Protection Regulation (GDPR), and notify the authorities if their systems become infected? That's potentially harder to answer.
"Arguably with ransomware, if you've got a backup and that data has been restored, has that happened and do you need to notify them of a breach? There's an argument that it's not necessary," said Wright.
However, there are scenarios where it's impossible not to envision the authorities not wanting to know if certain types of organisation have been breached: especially as critical infrastructure both becomes more reliant on internet-enabled control systems and increasingly comes under attack.
"If you're being told that unless you pay X amount of money then the entire energy system is being brought to its knees, then the UK government will demand to know about it," said Wright.