Why Does IT Hate Facebook and Twitter?

With as much as the media might talk about the "new enterprise" and "social media" you'd think that IT would be in lock-step with the rest of the businesswhen it came to social networking. But as my recent work with Michael Osterman shows, there's a big difference between applications that are allowed by organizations and the ones IT professionals consider to be legitimate.
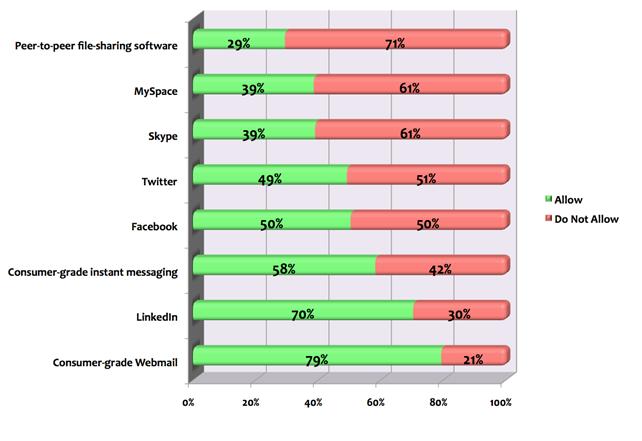
Osterman Research surveyed IT organizations of all sizes from across a wide range of industry. While half of the responding organizations allowed Facebook (Figure 1), only 28 percent of respondents thought the application to be legitimate (Figure 2). The same goes for Twitter, which was allowed by 49.2 percent of the organizations and yet viewed as illegitimate by just 28.3 percent of respondents.
Both Facebook and Twitter offer potential marketing value for organizations and Facebook in particular has a deep foothold into businesses today. Yet, IT still remains suspect of the applications. Perhaps that's because these are consumer application and IT is never thrilled with security and availability of consumer applications. Twitter, for example, has been the subject of Cross Site Request Forgery (CSRF) attacks that allowed site owners to acquire the Twitter profiles of their visitors.
Regardless, as marketing departments embrace blogging and micro-blogging, IT must find a way to close the gap around these applications. If these applications truly pose a threat to the organization then IT should provide corporate sanctioned versions of these applications, as was done with IM and file transfer. Otherwise, IT best adopt the applications as part of a broader IT solution set and learn to offer social media as an extension of its own offers.
Figure 1: Applications Allowed and Not Allowed
Figure 2: Legitimate and Non-Legitimate Applications