Why is Java so insecure? Buggy open source components take the blame

Veracode reckons 97 percent of the Java apps it examined contained at least one component with a known vulnerability.
Open-source and Java components used in applications remain a weak spot for the enterprise, according to a new analysis.
Java applications in particular are posing a challenge, with 97 percent of these applications containing a component with at least one known vulnerability, according to a new report from code-analysis security vendor Veracode.
Veracode's annual security report is based on 300,000 assessments it has run on enterprise applications over the 18 months to March 31, 2016, and includes software from open-source projects, commercial vendors, large and small businesses, and software outsourcers.
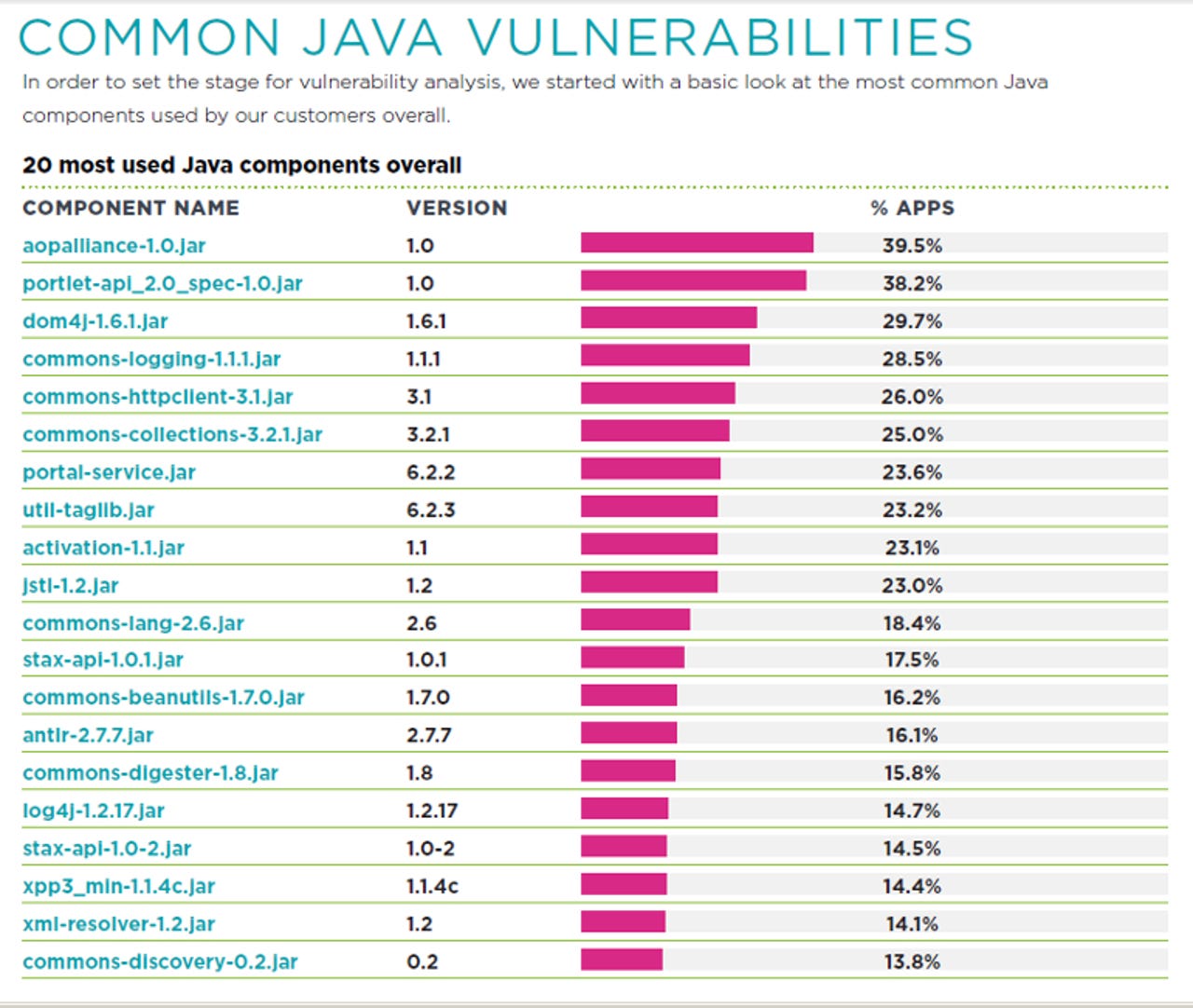
The most common bug it has found in Java applications is a vulnerable version of a component called Apache Commons Collections, present in 25 percent of the Java applications it scanned.
This issue, a deserialization vulnerability that allowed remote code execution, came to light in November after researchers published exploits using the bug for JBoss, IBM WebSphere, Jenkins, OpenNMS, and the Oracle WebLogic server.
"The Java deserialization vulnerability in Apache Commons Collections is an interesting example of an open-source, third-party component vulnerability, because it went from unknown to critical and highly exploitable, and because it was widely used in a variety of standard 'infrastructure' applications; web servers, application servers, CI servers," noted Veracode.
"It's worth noting that the issue was not just in the infrastructure applications, but in any application that uses Apache Commons Collections v.3.0 - 3.2.1 or 4.0. Addressing this vulnerability requires a broader response than just patching servers; it requires visibility into the component supply chain for all your applications."
The company also takes a swipe at assurances from commercial vendors that their products are free from vulnerabilities.
Veracode found that 39 percent of applications developed internally by organizations complied with the OWASP top 10 project standard, compared with just 25 percent commercially-developed applications submitted on behalf of enterprise users.
"This finding puts to bed vague vendor hype around unsubstantiated efforts to build assurance into their products. It reaffirms the need for organizations to demand better proof of software security from their vendors and to perform due diligence around all applications, including commercial software," Veracode said.
The most common vulnerabilities in applications include information leakage and cryptographic issues, which affected 72 percent and 65 percent of applications.
It also found that just over a third of all applications had hard-coded passwords, while 39 percent used broken or risky cryptographic algorithms.