IE9 versus Chrome: which one blocks malware better?

Last week I looked at a fascinating sample of malware that specifically targeted users of Google Chrome. Over the past few days, I’ve been looking more closely at this particular malware attack, which appears to be widespread and extremely persistent.
Social engineering has become the dominant method of distribution for fake antivirus software. And most modern browsers, with one exception, do a terrible job of dealing with this type of threat. Current builds of Chrome display a terrible flaw that puts you at greater risk than its competitors. In my testing, a malware author was able to exploit Chrome in four easy clicks. In stark contrast, Internet Explorer 9 used some new technology to flag the exact same sites and files as suspicious, providing unmistakable warnings that have been shown to stop 95% of these attacks in their tracks.
I’ve captured the experience for both browsers in these two videos and in an accompanying screenshot gallery so you can see for yourself. And if you make it to page 3, you'll read about the new reputation-based technology that's given IE9 the lead.
First a little background. Fake antivirus software has been around for at least seven years, but this category of attack has exploded in popularity among bad guys in recent months. The technique is simple social engineering, and it works by scaring the target into thinking their system has been infected with a virus (or a whole bunch of them) and then offering to fix the problem—for a fee. The fake AV software often downloads additional Trojans and can actually cause the sort of problems it claims to be solving.
Here’s how it goes when you’re using Google Chrome 10 on Windows 7. Notice the attention to detail that the malware authors used in this attack. The dialog boxes and warning screens certainly look like they’re part of Google Chrome. (I recommend clicking the full-screen button in the lower right corner of the video clips below so you can see all the details in each one.)
Now here’s an attack from the same set of search results, this time gathered using Internet Explorer 9. The fake scan is a pretty decent imitation of a Windows 7 security screen. But the result is different.
This particular attack represents the current state of the art for malware distribution. There are probably thousands of legitimate domains that have been hijacked to host these links—they’re the ones that show up in search results. The domains they redirect to are hosting the malware. Over the course of the past four days I have watched these malware domains change over and over again. As one is shut down, another takes its place. And the Trojan executables are mutating very rapidly, perhaps even hourly. Antivirus signatures are not able to detect the mutated strains until they’ve been in the wild for a day, by which time they’ve already been replaced.
This is a huge problem. According to data that Microsoft has gathered from billions of downloads over the past two years, roughly 1 out of every 14 program downloads are later identified as malware.
So how do you stop this sort of attack? Google and Microsoft are taking different approaches, with very different results.
Page 2: Why antivirus software can't keep up -->
<-- Previous page
Zero-day exploits get all the sexy headlines, but social engineering gets most of the results. And the bad guys have figured that out, devising a playbook that is rendering most antivirus software useless.
As I noted last week, a 2010 study by AVG found that social engineering attacks outnumbered direct exploits by a ratio of 4:1. A similar study by Google researchers analyzed fake AV distribution (here’s the full report, in PDF format) and found that up to 90% of all domains involved in distributing fake antivirus software used social engineering techniques.
The example I showed the other day involved a fairly esoteric search term: Silverlight datagrid reorder columns
But that wasn’t just a random, isolated example. With a little research, I was able to find other, similar terms that produced links to compromised sites. When I searched for custom asp datagrid open source, flash 8 datagrid headerrenderer, datagrid perl tk selectionset, or datagrid view column sort event, I found multiple examples of sites that led to fake AV software. Using lists of similar search terms that I culled from some unsavory sources, I am confident that I can reproduce these results with hundreds or even thousands of search terms.
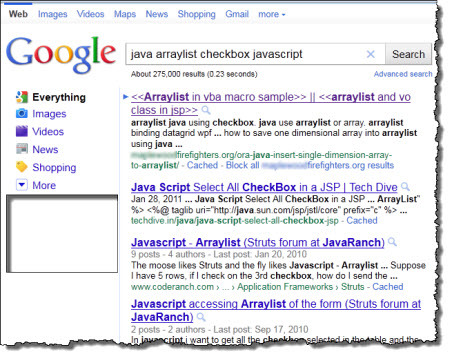
Bing is not immune from this type of “search engine poisoning,” but it appears that the bad guys have done a particularly effective job in targeting Google. For one Google search that I conducted over the weekend, java arraylist checkbox javascript, the top search result led to a compromised malware attack. Here’s the proof:
Google Image search results are even worse. Two image searches I performed at google.com led to poisoned results. Here are the search terms and the results:
- H628 Logitech Two results in the first 15 were poisoned with malware. A third was suspicious, but whoever planted the attack code on the compromised website had broken the site, so that attack failed.
- Yuri Gagarin The first Russian cosmonaut was in the news recently for the 50th anniversary of Sputnik. Two images in the first 20 Google Image search results were poisoned with malware, and a third led to a fraudulent online casino. I captured this attack on video as well.
Every one of these attacks follows the same pattern:
- You do a search and then click a link in a set of search results.
- The link from the search engine results leads to a page on a website that has been taken over by an outside attacker so that it runs a snippet of JavaScript. (If you enter the URL of that page directly, you bypass the redirect and get a mishmash of images and text and search terms.)
- The JavaScript redirects your browser to a site that hosts the malware. The landing page runs a social engineering attack—a fake “security scan” that purports to show that your computer is infected with multiple viruses.
- When the script finishes running, a dialog box offers to help you “remove” the infections. In reality, just about anything you do at this point will attempt to download the malicious software.
So, what’s a browser maker to do? The malware is so fresh that your up-to-date antivirus software doesn’t detect it yet. Here’s where Chrome and IE9 take very different approaches.
Page 3: How do you disrupt social engineering? -->
<-- Previous page
Google Chrome handles unknown executables the same way Internet Explorer 8 and Firefox do. It allows you to save the file locally, and then you can decide whether to run it. If the social engineering did its job, that means that a significant number of people are going to choose wrong.
Google Chrome frequently allowed me to save what turned out later to be malware. In a few cases I received a warning, but more often the executable file was simply downloaded and allowed to sit in the download bar at the bottom of the browser window. Here are the two download prompts I saw in Google Chrome, taken literally moments apart and representing tiny variations on the exact same dangerous executable.
In some cases, just clicking the plain white background of a hijacked web page caused Chrome to download a file and save it in the Downloads folder. Because this is an executable file simply clicking its entry in the Chrome downloads bar causes it to run. In the video I showed here, that took only four clicks, none of which offered any information to help me make a smart decision.
So how is Internet Explorer 9 different? Every download request gets passed through Microsoft’s SmartScreen filters. Google does something similar. But the IE9 version of SmartScreen includes a new set of algorithms designed to test the reputation of this executable file. Has it been seen before? Is there anything about the file name or the domain that looks suspicious?
In fact, one of the most important questions to ask is this one: Is the executable file digitally signed? Microsoft’s researchers found that roughly 96% of all those red warnings are attached to unsigned, previously unseen files. The algorithm assumes that a file—signed or unsigned—is untrustworthy until it establishes a reputation. No domain or file gets a free pass—not even a new signed release from Microsoft or Google. Every file has to build a reputation.
Update: The following paragraph has been expanded since its initial publication to clarify one important details of the reputation building process. For more details, see this post at the IE blog.
Software developers take note: The quickest way to build a positive reputation is to sign your executable files. Files inherit the reputation of the certificate used to sign them. A well-known, well-trusted digital certificate adds enough reputation credit to give a digitally signed file from a legitimate domain a positive reputation immediately. Unsigned files from unknown domains automatically get red-flagged and typically stay that way.
This approach turns conventional thinking on its head, but from a security perspective it’s the right thing to do. It deals with the problem of “dialog box fatigue" by reserving the most dire warnings for files that are new and unknown. Microsoft says that its data show the risk of being infected with malware from clicking through one of these “unknown file” warnings is at least 25% and possibly as high as 70% on any given day. Legitimate files quickly establish a reputation and no longer produce a warning. Actual malware quickly gets identified within a day or two and is fully blocked around the same time the hosting site gets shut down.
According to data that Microsoft gathered during beta testing of IE9, this approach has had a profound impact on user behavior. Fully 95% of previously undetected malware is now either deleted or not run by the user. The impact on actual infections is equally profound, with Microsoft data showing infection rates have dropped to 1/20th compared to similar rates for IE8.
This kind of improvement isn’t just a matter of clever code. It takes a tremendous investment in back-end services and a huge commitment of resources—people and money—to do the necessary analysis. This is one feature that other browser makers—especially Google—desperately need to copy.