Russian security firm says Flashback infection rates still high

Update: Symantec researchers confirm Dr. Web details. See end of post for details.
Last week the Mac community collectively breathed a sigh of relief when Symantec published a report that appeared to indicate that the Flashback malware epidemic appeared to have declined sharply.
In that report, Symantec said the number of infections had dropped to 380,000 on April 10 and to 270,000 on April 11. Kaspersky Labs reported a similar decline, with the number of infected computers dropping to 237,000 according to its monitoring.
But the Russian security company that first reported the news that a massive number of Macs had been infected said today that Symantec’s monitoring tools are mistaken. Not only has the infection rate not declined, says Dr. Web, but new infected computers are continuing to join the botnet daily.
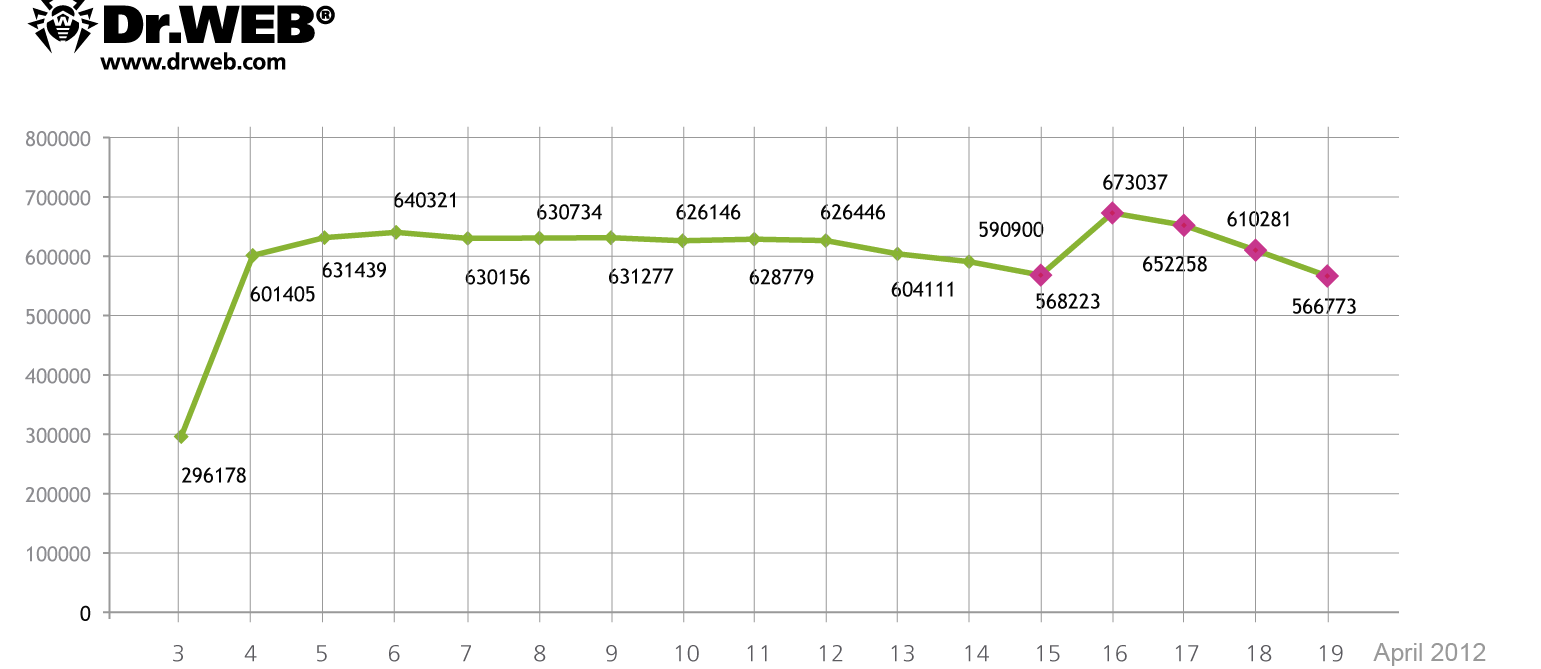
According to Doctor Web, 817 879 bots connected to the BackDoor.Flashback.39 botnet at one time or another and average 550 000 infected machines interact with a control server on a 24 hour basis. On April 16, 717004 unique IP-addresses and 595816 Mac UUIDs were registered on the BackDoor.Flashback.39 botnet while on April 17 the figures were 714 483 unique IPs and 582405 UUIDs. At the same time infected computers, that have not been registered on the BackDoor.Flashback.39 network before, join the botnet every day. The chart below shows how the number of bots on the BackDoor.Flashback.39 botnet has been changing from April 3 to April 19, 2012.
Source: Dr. Web
Based on that chart, the net number of infections is dropping slowly, as existing Macs are cleaned up. But new infections are appearing at the same time. As of April 19, Dr. Web says there are still 566,000 infected Macs, based on unique IDs presented by the botnet members.
Why the discrepancy between the different researchers’ numbers?
According to Dr. Web’s research, the measurement process is straightforward, based on the observed behavior of infected machines:
BackDoor.Flashback.39 uses a sophisticated routine to generate control server names: a larger part of the domain names is generated using parameters embedded in the malware resources, others are created using the current date. The Trojan sends consecutive queries to servers according to its pre-defined priorities. The main domains for BackDoor.Flashback.39 command servers were registered by Doctor Web at the beginning of April, and bots first send requests to corresponding servers. On April 16th additional domains whose names are generated using the current date were registered. Since these domain names are used by all BackDoor.Flashback.39 variants, registration of additional control server names has allowed to more accurately calculate the number of bots on the malicious network, which is indicated on the graph.
So far, so good. But at that point one server, controlled by an unidentified third party, throws a monkey wrench into the data-collection routine:
However, after communicating with servers controlled by Doctor Web, Trojans send requests to the server at 74.207.249.7, controlled by an unidentified third party. This server communicates with bots but doesn't close a TCP connection. As the result, bots switch to the standby mode and wait for the server's reply and no longer respond to further commands. As a consequence, they do not communicate with other command centers, many of which have been registered by information security specialists. This is the cause of controversial statistics…
If those numbers are accurate, then Apple might have more work to do. So far, Apple has released three Java updates, the most recent of which is designed to clean infections from Macs running OS X Lion and Mac OS X 10.6 (Snow Leopard). But those updates are only effective if they’re installed, and security researchers have long noted that users avoid updates. In addition, roughly 17% of Mac users, or a total population of more than 10 million, are running older versions of OS X that are not eligible for any security updates and can only protect themselves by completely disabling Java.
I have contacted Symantec and Kaspersky and will update this post when I hear back from those companies.
Update 20-Apr 1:35PM PDT: In a blog post update, Symantec researchers confirm the observation by Dr. Web:
A recent Dr. Web blog post reveals our sinkholes are receiving limited infection counts for OSX.Flashback.K.
Our current statistics for the last 24 hours indicate 185,000 universally unique identifiers (UUIDs) have been logged by our sinkhole.
A sinkhole registered at IP address 74.207.249.7 is causing Flashback connections to hang as it never closes the TCP handshake, in effect preventing Flashback from hitting subsequent domains.
See also: