Flame: 'Most complex' cyber-attack ever discovered

Security researchers have discovered a new 'data-vacuuming' malware which has targeted a number of Middle Eastern countries including Israel and Iran.
Kaspersky said it believes "Flame" is larger than its apparent infamous counterparts Stuxnet and Duqu, and has been described as the "most complex threat" ever discovered.
Kaspersky's Alexander Gostev said in an extensive questions and answers SecureList blog post that Flame "redefines the notion of cyberwar and cyberespionage".
Flame is an attack toolkit --- rather than a 'throwaway' single-operating piece of malware --- like Stuxnet and Duqu --- which has the ability to relay back through the "eyes and ears" of a computer.
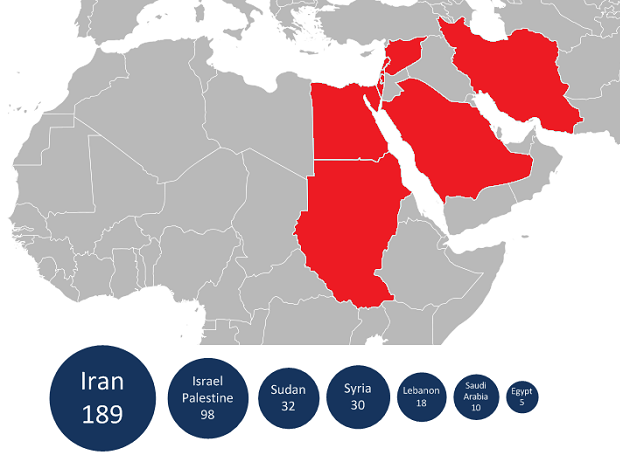
Along with Iran and Israel, Sudan and Syria found infected networks, as did Lebanon, Saudi Arabia, and Egypt. Others have been infected but Kaspersky did not name the individual countries.
Reutershowever reports that Kaspersky's Roel Schouwenberg, who discovered the malware, said Flame was "highly targeted" and directed at businesses and universities, adding: "no more than 5,000 personal computers around the world have been infected, including a handful in North America."
Iran's National Computer Emergency Response Team updated its security alert pages stating it believed Flame was the cause of a number of incidents of "mass data loss" in the country's computer networks.
Flame has the components of a Trojan, a backdoor, and a worm, and is designed to attack Windows machines. Researchers do not appear to know how Flame initially enters a network, but have identified a Windows vulnerability that the malware exploits.
Compared to Duqu's 300KB payload versus Stuxnet's 500KB payload, Flame is a massive 20MB in size. Wired explains that Flame does not resemble either Stuxnet or Duqu in "framework, design or functionality," despite their on-the-surface properties and similarities.
Flame sniffs network traffic and has the ability to take screenshots, record conversations by microphones that are plugged in or embedded to the PC, and keylogs input data and so forth.
The malware is unique in that it has the ability to steal so much data in so many different ways, allowing a complete overview in "eyes and ears" of anything and everyone in the vicinity of the infected machine.
Kamluk said the "size and sophistication" of Flame makes it more likely to be government-backed. Considering the malware has been designed to target Israeli networks, an allied nation to the U.K. and the U.S., the attack is unlikely to originate from the West.
Gostev explained in a SecureList posting:
"Currently there are three known classes of players who develop malware and spyware: hacktivists, cybercriminals and nation states. Flame is not designed to steal money from bank accounts. It is also different from rather simple hack tools and malware used by the hacktivists,"
"By excluding cybercriminals and hacktivists, we come to conclusion that it most likely belongs to the third group. In addition, the geography of the targets (certain states are in the Middle East) and also the complexity of the threat leaves no doubt about it being a nation state that sponsored the research that went into it."
In 2010, Stuxnet was used to attacked Iranian nuclear facilities, while Duqu --- found spreading exactly a year later in 2011 --- was used to infiltrate networks and steal corporate and government data.
Kapersky believes that the original creation of the Flame project began no earlier than 2010, which coincides with the discovery of the security loophole it exploits.
ZDNet's Charlie Osborne contributed to this report.
Image credit: Kaspersky Lab.
Related:
- UK government ‘planning to launch Stuxnet-like attacks’ against hostile states
- ZDNet Zero Day: CBS 60 Minutes: Stuxnet worm opens new era of warfare
- Stuxnet 2.0? Researchers find new 'cyber-surveillance' malware threat
- Hungarian Lab found Stuxnet-like Duqu malware
- ZDNet Government: Stuxnet may be the Hiroshima of our time
- CNET: Stuxnet delivered to Iranian nuclear plant on thumb drive
- Ex-CIA chief: Stuxnet a good idea
- CBS News: Video: Is Duqu the progeny of Stuxnet?