LinkedIn password breach: How to tell if you're affected

LinkedIn customers are still reeling after the news broke that hackers had accessed a vast cache of passwords to the "professional social network".
More than 6.46 million people are thought to be affected or around 5 percent of the site's 150 million users. LinkedIneventually confirmed a breach and said affected users would have their accounts locked, and an email would be sent out asking for a password change.
Users are advised to change their LinkedIn password immediately.
In cases like this, it's often tricky to know whether your account details have been leaked without downloading the dump file and trawling through it. Thankfully, "there's an (web) app for that."
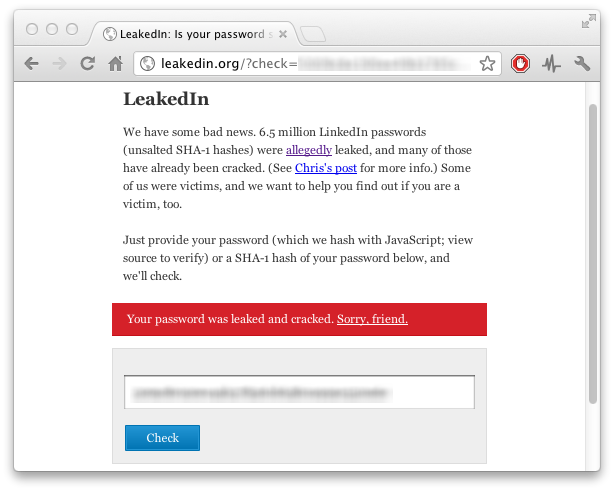
Developers Chris Shiflett, Sean Coates, and Bedrich Rios developed in only a few hours a way to check to see whether your LinkedIn password had been leaked. After the discovery, he took the dump of passwords --- since removed from its original location, though still widely available on the Web --- and created LeakedIn.org.
Simply type in your LinkedIn password and it will tell you whether you're in the unlucky 5 percent.
I know what you're thinking: "Type in my potentially already leaked password into a random site? You have to be kidding." The site uses JavaScript to hash your password, and because it uses only client-side code, your password never actually leaves your computer.
Of course, this is merely a way of seeing whether your password was breached. Other services are popping up around the web. Another from LastPass also works effectively, and many may feel more comfortable using a tool from a company they already own products from.
These password checkers in reality give you two options:
Firstly, it sends back a clear message on whether you need to change your LinkedIn account password --- which you are advised to do anyway. It's safe to at least assume the hackers have your corresponding email address as well, though this has yet to be confirmed by the company.
Secondly, if you happen to use that password on another service, a nod to change that service's password too. It's never a wise idea to use the same password twice in case one account is breached --- despite most people doing so --- so stop reading this and go and change your password.
Image credit: LeakedIn.org/ZDNet.
Related: