Researchers crack WPA Wi-Fi encryption in 60 seconds

Computer scientists in Japan have developed a way to break the WPA encryption system used in wireless routers in just one minute.
The attack, which reads encrypted traffic sent between computers and certain types of routers that use the WPA (Wi-Fi Protected Access) encryption system, was devised by Toshihiro Ohigashi of Hiroshima University and Masakatu Morii of Kobe University.
The scientists plan to discuss further details at a technical conference on Sept. 25 in Hiroshima.
Security researchers first showed how WPA could be broken last November, but the researchers have accelerated theory into practice, taking the proven 15-minute "Becks-Tews method" developed by researchers Martin Beck and Erik Tews and speeding it up to just 60 seconds.
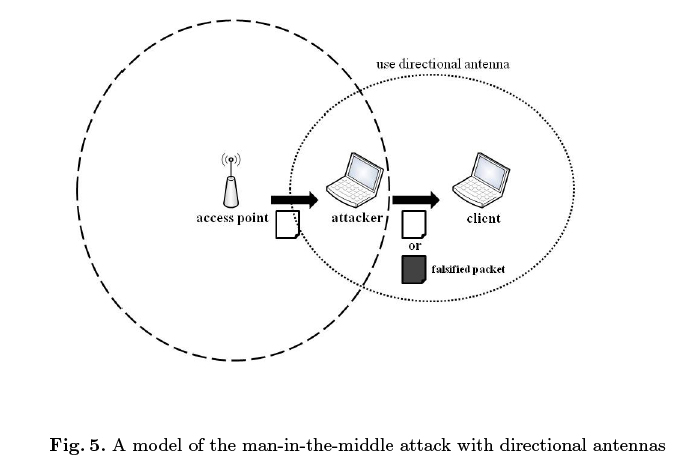
Both attacks work only on WPA systems that use the Temporal Key Integrity Protocol (TKIP) algorithm, and do not work on newer WPA 2 devices or on WPA systems that use the stronger Advanced Encryption Standard, or AES, algorithm.
According to their report (.pdf), the limits of the man-in-the-middle attack are fairly restrictive. But the development should spark users to drop WPA with TKIP as a secure method of protection.
Securing routers has been a long and bumpy road. The WEP (Wired Equivalent Privacy) system introduced in 1997 is now considered to be insecure by security experts. Then came WPA with TKIP, followed by WPA 2.
But users have been slow to upgrade to the latest secure methods.