Stuxnet: Future of warfare? Or just lax security?

The Stuxnet worm has hit the big time after Iranian officials confirmed that the malicious code was wreaking havoc at the country's first nuclear power station.
This malware, which surfaced back in July, can take over industrial operating systems---known as SCADA---and control plants. Roughly 15 systems have been infected globally. The first reaction to the Iran malware woes is that it couldn't have happened to a nicer country. But then you realize that Stuxnet could really just be the start of cyberwarfare and key infrastructure is at risk.
Questions abound about Stuxnet? Did Israel plant the virus? How about the U.S.? Or is Iran just behind the Stuxnet like the other countries that have seen the virus? These questions have been brewing for weeks and came to a boil over the weekend. In any case, every utility company and the Department of Homeland Security are looking out for it. The Pentagon is supposed to have a Cyber Command ready next month. Other agencies remain vulnerable.
Needless to say there have been a bevy of Stuxnet headlines:
- BBC: Stuxnet worm hits Iran nuclear plant staff computers
- WSJ: Cyber Attacks Test Pentagon, Allies and Foes
- AP: Worm hits computers of staff at Iran nuclear plant
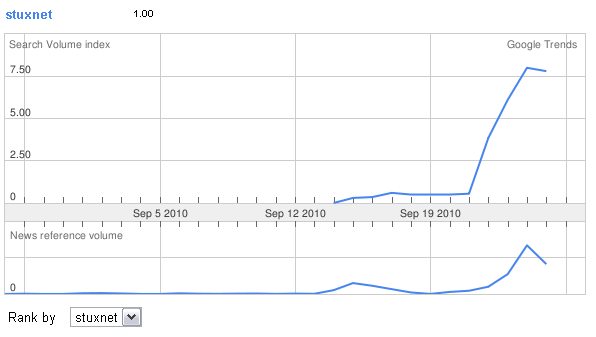
Here's the Google Trend data for Stuxnet.
What we may be seeing is the precursor to the new age air attack---viruses hitting key infrastructure like electric grids, plans and other key systems. In addition, Stuxnet is rather elegant so perhaps it was state sponsored. Sophos notes:
Stuxnet is a highly sophisticated piece of malware, which used a number of techniques which hadn't been seen before (for instance, exploiting zero day vulnerabilities in Microsoft's code).
Ryan Naraine noted earlier this month:
The attackers behind the recent Stuxnet worm attack used four different zero-day security vulnerabilities to burrow into — and spread around — Microsoft’s Windows operating system.
The other key thread here focuses on the preparation for Stuxnet.
Also see: Should a targeted country strike back at the cyber attackers?
1. The virus has been isolated on a test system in order to carry out more extensive investigations. Previously analyzed properties and the behavior of the virus in the software environment of the test system suggest that we are not dealing with the random development of one hacker, but with the product of a team of experts who must have IT expertise as well as specific know-how about industrial controls, their deployment in industrial production processes and corresponding engineering knowledge. 2. As far as we know at the moment, industrial controls from Siemens are affected. The Trojan is activated whenever WinCC or PCS7 software from Siemens is installed. 3. Further investigations have shown that the virus can theoretically influence specific processes and operations in a very specific automation environment or plant configuration in addition to passing on data. This means that the malware is able, under certain boundary conditions, to influence the processing of operations in the control system . However, this behavior has not yet been verified in tests or in practice. 4. The behavioral pattern of Stuxnet suggests that the virus is apparently only activated in plants with a specific configuration. It deliberately searches for a certain technical constellation with certain modules and certain program patterns which apply to a specific production process. This pattern can, for example, be localized by one specific data block and two code blocks. 5. This means that Stuxnet is obviously targeting a specific process or a plant and not a particular brand or process technology and not the majority of industrial applications. 6. This conclusion also coincides with the number of cases known to Siemens where the virus was detected but had not been activated, and could be removed without any damage being done up to now. This kind of specific plant was not among the cases that we know about.
However, Sophos notes that Siemens' advice isn't perfect.
Stuxnet knows the default password used by the Siemens SCADA software, but - astonishingly - Siemens advised power plants and manufacturing facilities not to change their default password. That's despite it being public knowledge on the web for some years.
In any case, Microsoft Patch KB2347290 has been successfully tested on Siemens SCADA systems. Add it up and all this spy vs. spy talk may just be a case of lax patching procedures. Microsoft shipped an emergency patch and then an official one, but could have squashed Stuxnet earlier. See:
- Patch Tuesday recap: Exploits expected for Windows security holes
- Stuxnet attackers used 4 Windows zero-day exploits
- As attacks escalate, Microsoft ships emergency Windows patch
Related: