Software that automatically fixes itself, without shutting down

Software vulnerabilities that take days or weeks to fix may one day be a thing of the past. A team of researchers have presented new software, called ClearView, that automatically patches errors in deployed software in a matter of minutes.
As Technology Review reports, ClearView works without assistance from humans and without access to a program's underlying source code. Instead, it monitors the behavior of a binary: the form the program takes in order to execute instructions on a computer's hardware.
A paper, Automatically Patching Errors in Deployed Software, published by the Association for Computing Machinery, explains how ClearView works as five sequential steps:
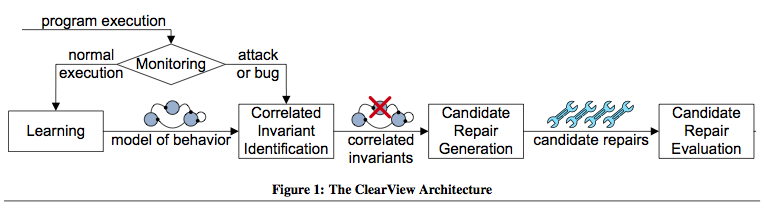
- It observes normal executions to learn invariants that characterize the application's normal behavior
- Uses error detectors to distinguish normal executions from erroneous executions
- Identifies violations of learned invariants that occur during erroneous executions
- Generates candidate repair patches that enforce selected invariants by changing the state or flow of control to make the invariant true, and;
- Observes the continued execution of patched applications to select the most successful patch
In other words, by observing a program's normal behavior and assigning a set of rules, ClearView detects certain types of errors, particularly those caused when an attacker injects malicious input into a program. So when something goes amiss, ClearView detects the anomaly and identifies the rules that have been violated. And then it comes up with several potential patches that are applied directly to the binary (rather than access the source code) to force the software to follow the violated rules. ClearView analyzes these possibilities to decide which are most likely to work, then installs the top candidates and tests their effectiveness. And If additional rules are violated, or if a patch causes the system to crash, ClearView rejects it and tries another. The process is illustrated below:
With this approach, ClearView can detect errors and provide for an automatic fix that doesn't require restart nor interrupt the execution, making it well-suited to correct errors in software with high availability requirements.
According to Martin Rinard, a professor of computer science at MIT, ClearView could be used to fix programs without requiring the cooperation of the company that made the software, or to repair programs that are no longer being maintained. He hopes the system could extend the life of older versions of software, created by companies that have gone out of business, in addition to protecting current software, writes TR.
To test the system, the researchers (most from MIT) brought in an independent team to attack a group of computers running Firefox. The team developed ten code injection exploits and used these exploits to repeatedly attack an application protected by ClearView. ClearView successfully detected and fended off the would-be attacks. For seven of the ten exploits, ClearView automatically generated patches that corrected the error, enabling the application to survive the attacks and continue on to successfully process subsequent inputs.
Finally, the independent team attempted to make Clear-View apply an undesirable patch, but ClearView's patch evaluation mechanism enabled ClearView to identify and discard both ineffective patches and damaging patches.
The work was presented earlier this month at the 22nd ACM Symposium on Operating Systems Principles.
For more technical information consult the PDF and slides presented.