Cheap GPUs are rendering strong passwords useless

Think that your eight-character password consisting of lowercase characters, uppercase characters and a sprinkling of numbers is strong enough to protect you from a brute force attack?
Think again!
Jon Honeyball writing for PC Pro has a sobering piece on how the modern GPU can be leveraged as a powerful tool against passwords once considered safe from bruteforce attack.
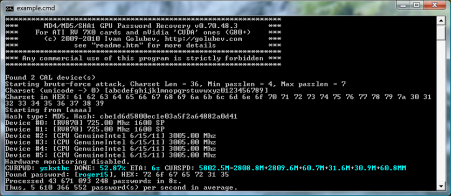
Take a cheap GPU (like the Radeon HD 5770) and the free GPU-powered password busting tool called 'ighashgpu' and you have yourself a lean, mean password busting machine. How lean and mean? Very:
The results are startling. Working against NTLM login passwords, a password of "fjR8n" can be broken on the CPU in 24 seconds, at a rate of 9.8 million password guesses per second. On the GPU, it takes less than a second at a rate of 3.3 billion passwords per second.
Increase the password to 6 characters (pYDbL6), and the CPU takes 1 hour 30 minutes versus only four seconds on the GPU. Go further to 7 characters (fh0GH5h), and the CPU would grind along for 4 days, versus a frankly worrying 17 minutes 30 seconds for the GPU.
It gets worse. Throw in a nine-character, mixed-case random password, and while a CPU would take a mind-numbing 43 years to crack this, the GPU would be done in 48 days.
Surely throwing symbols in there keeps you safe, right? Wrong! Take a password consisting of seven characters, mixed-case/symbols random password like 'F6&B is' (note the space), that's gotta be tough for a bruteforce attack. Right? A CPU will take some 75 days to churn through the possibilities, while a GPU is done with it in 7 hours.
What's the solution? Well, Honeyball doesn't know, and neither do I to be perfectly honest. What I do know is that this is a warning, and one that we need to take seriously. Unless we're willing to move onto 15-16 characters, mixed-case/symbols random password (which will end up on Post-It Notes), passwords will soon only offer protection against honest people.
[UPDATE: Take a look at this - whitepixel 2 running with 4 x HD 5970 cards (8 x GPUs) capable of 33.1 billion MD5 password hashes/sec.
Via: SimonZerafa of PC-Technical]