Report finds Firefox security lacking

A report by security firm Accuvant finds Mozilla's Firefox lacking when it comes to modern security safeguards.
The report (available here) finds that Firefox lags behind Google's Chrome and Microsoft's Internet Explorer browsers in several key areas.
Note: The report was funded by Google, but Accuvant is a well-respected security firm and the report appears to be both fair and accurate.
Here are a few example:
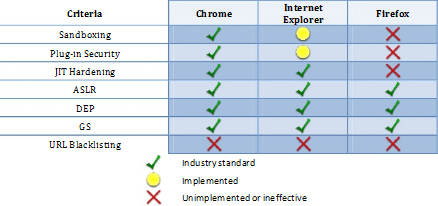
According to the report Firefox security was found lacking in three key areas:
- Sandboxing - A technology which limits how much access an exploit has to the target machine.
- Just-In-Time (JIT) hardening - Technology which prevents malicious JavaScript code on a website from compiling code on the target computer.
- Plug-in security - This limits how much access plug-ins have and also prevents the download of malicious add-ons.
Firefox also topped the list when it came to critical vulnerabilities.
The conclusions of the report won't make comfortable reading for Firefox fans:
Both Google Chrome and Microsoft Internet Explorer implement state-of-the-art anti-exploitation technologies, but Mozilla Firefox lags behind without JIT hardening. While both Google Chrome and Microsoft Internet Explorer implement the same set of anti-exploitation technologies, Google Chrome’s plug-in security and sandboxing architectures are implemented in a more thorough and comprehensive manner. Therefore, we believe Google Chrome is the browser that is most secured against attack.
Accuvant has made its data and test tools available for download to anyone interested.
If you're interested in security, Firefox might not be the right browser for you.