Your passwords don't suck, it's your policies

Passwords stink because policies for creating them typically focus only on composition and can't measure strength, according to developer Cameron Morris.
The time it takes to crack a password is the only real way to determine its strength and value, said Morris, a developer at defense contractor Partnet.
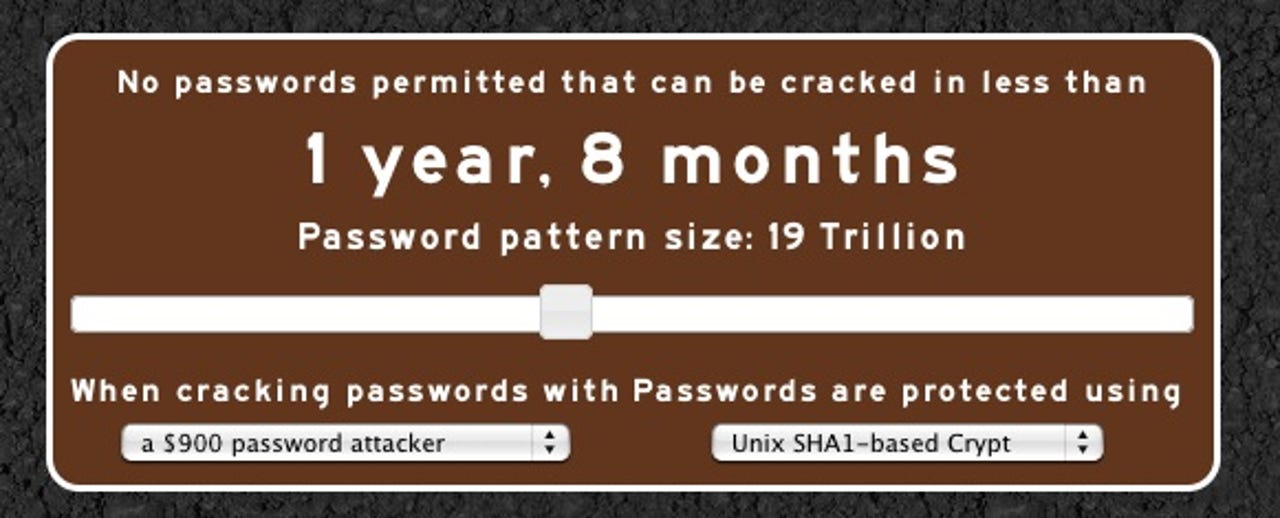
And to prove it, he created an open-source tool called Passfault that predicts the time it takes to crack a specific password. And he invites administrators and end-users to try both the Analyzer and the Password Creation Slide-Tool.
"I had spent 30 minutes creating a password that would be hard to crack, but then I realized it would expire in 30 days," said Morris, who began building his tools three years ago. "I thought wouldn't it be neat to set password expiration based on how strong your password is, but I couldn't find a way to measure that," he said.
In January, Morris turned his Passfault project over to the non-profit Open Web Application Security Project (OWASP) in the hopes a community of developers will help improve the software, add new languages and expand its dictionaries.
He currently has Java and JavaScript Object Notation (JSON) versions and is planning a JavaScript version.
Morris is challenging common notions about creating strong passwords by examining patterns instead of using policies based on letters, numbers and special characters.
A 2011 Carnegie Mellon University study showed that password creation policies actually made it harder to create a strong password and that password length was the only significant variable influencing strength.
Morris's goal is to make password strength measurable and easily understood. Passfault shows that the right patterns beat a capital letter and an ampersand every time, he says.
Passfault identifies dictionary patterns (English, Spanish) including mixed cased words, substituted or inserted special characters, misspellings, and words spelled backward. It also examines keyboard patterns (U.S. and Russian), including horizontal and diagonal sequences and repeated keys; and data patterns.
Passfault examines a password then calculates the number of passwords that could exist with similar patterns. Morris calls it the "measurement of password complexity."
Passfault's Analyzer spits out a "time-to-crack" grade after a user enters their password. Time-to-crack represents how many passwords fit in a particular pattern. The slider tool lets admins calculate strength by pattern size, type of password protection, and an estimate of cracking hardware used by hackers.
He chuckles at Facebook's grade of "weak" for the 35-character password Morris created using the first letters of a random phrase, as compared to Facebook's "strong" rating for a password that fit its creation policies but uses the common word "cracked" followed by a ‘1' and a ‘!'
The pattern of the latter can be cracked in less than a day, according to Passfault.
Time-to-crack evaluations, he says, identify weakness and expose the true risk passwords pose to a company or organization.
Of course, Passfault is only about creating passwords, not protecting them. Recent hacks have resulted in the theft of passwords from company databases, including well-publicized hacks of Sony and Zappos. One issue is that end-users typically re-use passwords on multiple sites, which increases exposure if their credential is stolen.
A standards effort called OpenID is advocating that Web sites get out of the password business and rely on a set of identity providers that would validate credentials for users visiting their sites.
Passfault could potentially help those providers combine more secure passwords with their ability to protect the credential itself. And it also is aimed at enterprises who want to minimize risk and help end-users create strong passwords.
"I have a Google Alert on password strength, and it's fun to see people giving advice," says Morris. "The Passfault approach changes the advice we should give out."
See also: