The Air Force's secure Linux distribution

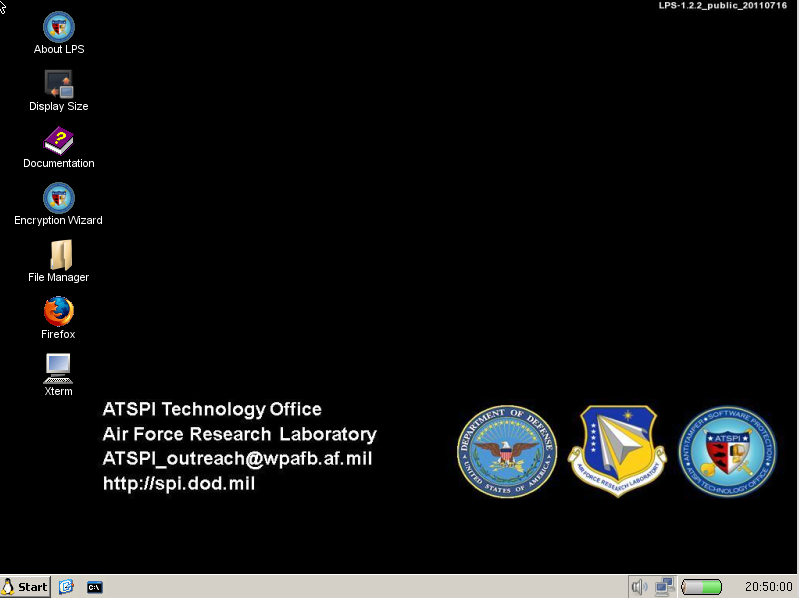
The Software Protection Initiative (SPI) under the direction of the Air Force Research Laboratory and the US Department Of Defense recently created Lightweight Portable Security (LPS). Like the name indicates, this is a small Linux desktop distribution that's designed for secure use.
LPS is designed to boot from a CD or USB pen-drive on any Intel-based computer. It doesn't install anything. It's designed solely to run solely in memory and to leave no traces behind when you're doing running it.
According to the SPI, LPS "allows general Web browsing and connecting to remote networks. It includes a smart card-enabled Firefox browser supporting Common Access Card (CAC) and Personal Identity Verification (PIV) cards, a PDF and text viewer, Java, and Encryption Wizard - Public." With it you can turn your untrusted Windows or Mac home or public system into a trusted network client. "No trace of work activity (or malware) can be written to the local computer."
It's not your usual operating system in other ways as well. "LPS isn't meant to be patched. When it's updated, you need to download a new virgin copy of the operating system. LPS is updated at least every quarter. To get the best possible protection the SPI recommends you simply download a fresh copy of the distribution with every update.
LPS has a very simple interface based on the IceWM desktop. More than anything else LPS looks like Windows XP. As you'd expect from a "safety first" distribution, it comes with a minimum of applications. These include the older, but still essentially secure, Firefox 3.6.22 Web browser, the Leafpad text editor, and the OpenSSH secure shell client and Citrix XenApp client for running remote desktop sessions.
For some reason, the distribution also includes Adobe Flash. Considering Flash's recent checkered security record, I wouldn't have included it had this been my distribution.
The encryption wizard is simple for anyone over the age of eight to use. When you launch it, you get a small window where you can drag-n-drop files to work on. Once there, you have three large buttons at to choose from: "Encrypt," "Archive," and "Decrypt." I think anyone can handle that! There's also a Deluxe version of the distribution that comes with OpenOffice and Adobe Acrobat.
Is this distribution for everyone? Heck no. But, if you want a secure desktop operating system you can carry in your pocket and use on almost any computer you're likely to find, it's well worth burning to a CD or USB drive.
Related Stories:
The Linux desktop is dead. Long live the Linux desktop.
The Five Best Desktop Linux Distributions
What's coming in Ubuntu's new Unity Linux desktop