Japan's ISPs agree to ban P2P pirates

Four of Japan's largest Internet provider organizations have come to an agreement with copyright holders on how to tackle the illegal file trading on P2P (Peer to Peer) networks. Comprised of about 1000 major and smaller Japanese Internet providers, the four organizations agreed to target flagrant copyright violators by first warning them and then banning them if their behavior doesn't change.
According to the Daily Yomiuri Online, the Internet providers two years ago attempted to disconnect users anytime they detected the use of Winny (a popular Japanese P2P application) or any other file-sharing software. But that ran afoul of the Japanese Ministry of Internal Affairs and Communications because of concerns of privacy and the providers abandoned that practice. This time the Internet providers seem to have learned from the past and they're going to be much more targeted by going after the most obvious transgressors of illegal file trading.
When the copyright owners see a list of IP (Internet Protocol) addresses downloading their copyrighted content, they'll send that list of violators to the ISP (Internet Service Provider) and the ISP will warn and then ban the copyright infringers if necessary. This method doesn't involve any of that politically dreaded DPI (Deep Packet Inspection) since the copyright owner merely needs to look for their own content on the popular file trading sites and ask for a list of peers by merely participating in the file trade. Not only does this method avoid privacy concerns, it also happens to be the most practical if not the only way of attacking the problem since many file trading applications are already completely encrypted against packet snooping.
Update 5:40AM - Just to make myself extra clear since many people refuse to believe that we are not talking about deep packet inspection here. P2P in Japan like the latest "Perfect Dark" application (successor to Winny and Share) is already fully encrypted at both the protocol and data level. That's encryption is completely bypassed since the content owners merely need to download the Winny, Share, and Perfect Dark and look for their own content that's being pirated. Then all they need to do is connect to it as if they were a user and then download the content to see if it is indeed their content. Then they already have a list of IP addresses that participated in that file exchange. There's no decryption, key cracking, or deep packet inspection going on here.
Japan is considered one of the most connected broadband nations on the planet with widespread 100 Mbps broadband service. Many people in this country believe that by simply offering more capacity, there would be no need to manage the network since congestion problems would be gone. But Japan teaches us that no matter how much capacity you throw at the problem, congestion will always be a problem and the vast majority of it will be caused by P2P traffic.
At the iGrowthGlobal Panel on Network Management on Capitol Hill (my recap here), I met Haruka Saito who is Counselor for Telecom Policy from the Embassy of Japan. Mr. Saito was my fellow panelist and he shared the following data with the congressional and FCC staffers in the audience. He presented the following data from the Japanese Ministry of Internal Affairs and Communications which had been studying the issue of Net Neutrality in Japan for more than a year.
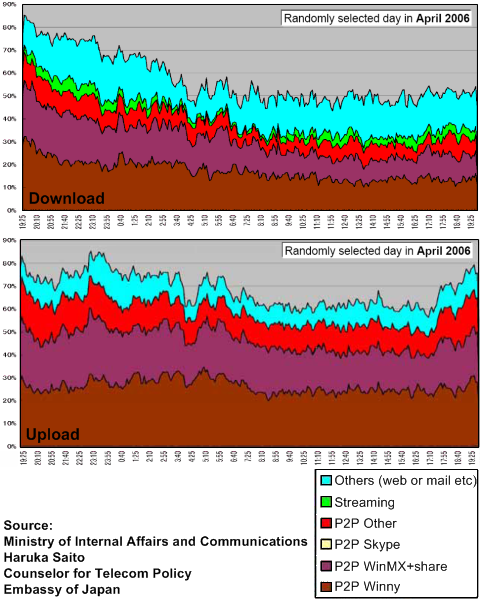
[Updated 3:15PM - I had incorrectly stated that 1% consumes 63% of all traffic because I read the charts wrong. The corrected text is in bold below.] As you can see, the utilization levels especially for uploads are dangerously high and that P2P traffic absolutely dominates both upload and downloads by a very large margin. Winny, WinMX, and Share (a successor of Winny) dominates the P2P usage. From this data, the P2P users that make up 10% of all Internet users in Japan hog ~75% of bandwidth resources and 1% of all Internet users in Japan consume 63% of that 75% share. That means just 1% of users consume 47% of all the Internet traffic in Japan. It's no wonder the ISPs in Japan want a solution that cuts off the most egregious illegal file traders who also happen to be the biggest bandwidth hogs.