Many Banks failing to use SSL authentication

In a recent SANS blog, the issue that many banks are using non-SSL login forms has raised some serious concerns about the lack of good Banking security. They even posted this Online Banking score board showing which Banks are practicing good security and which aren't.
What's actually happening is that Banks are using SSL for encryption, but they're not using it to prove the Bank's authenticity to you the customer. Encryption is useless if you don't know who you're talking to is the entity you're intending to talk to. This means that it's extremely easy to intercept and spoof a Bank that doesn't use SSL login forms. Unsuspecting users will login to a fake online Bank and enter their login credentials which get captured by the bad guys. Once they have it, they can just transfer some money to their own bank accounts.
Among the ones listed in the bad security category, American Express was one of them. Not only does American Express not use SSL authentication by default, but it uses a bad Digital Certificate even when you manually type in HTTPS in the address bar to force SSL authentication. You get the warning below that "the name on the security certificate is invalid or does not match the name of the site".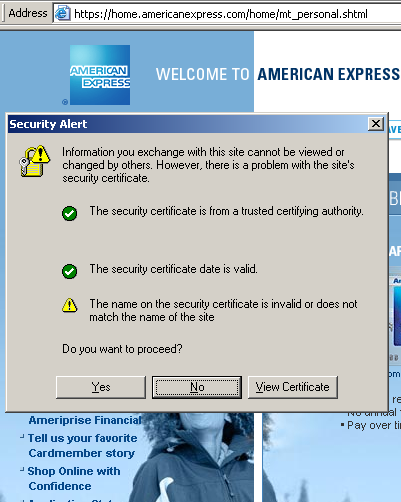
USA Banks failing to use SSL authentication includes:
- American Express
- Bank of America
- Chase
- Countrywide
- DCU
- Georgia Telco Credit Union
- Keybank
- NationalCity
- NAVY Federal
- PSECU
- US Bank
- Wachovia
- Washington Mutual
Outside of the USA, only HSBC fails to use SSL authentication though the list is still being updated. This looks really ugly for the American Banking system as a whole and it's time that they cleaned up their act and learn to use some basic cryptography. If you have a bank on this hall of shame list where "SSL Login Form" is listed as "optional", be sure to complain to them that this is unacceptable. I'll also be following up with these banks and if they don't do anything soon, I'll be sure to escalate the issue to the proper channels.