Attack of the Opt-In Botnets
What's more devastating than a DDoS attack launched by a botnet? In some cases, that's the DDoS attack launched by the "opt-in botnet" aggregated through a crowdsourcing campaign.
Damballa's recently released report "The Opt-in Botnet Generation: Social Networks, Cyber Attacks, Hacktivism and Centrally-Controlled Protesting" describes the increasing sophistication of cyber-protesting tools, for launching political protests around the globe.
Let's review seven well known and extensively profiled examples of "opt-in botnets" and crowdsourcing campaigns, to find out why some failed and others succeeded.
What exactly is an opt-in botnet? What are some of the most notable cases where it has been successfully used? How can you disrupt a opt-in botnet given that the command and control server is in the hands of every user knowingly participating in it?
Damballa's report describes "opt-in botnets" as:
- "In practically all criminal botnet cases in the past, the owners or users of the bot-infected computers have been unwitting participants in an attack. This aspect of botnet participation fundamentally changes in the context of cyber-protesting, since as users intentionally install botnet software agents, subscribe to a particular CnC, and choose to participate in coordinated attacks against a target category. Whether it’s because of a vagueness in the understanding of laws governing cyber attacks and electronic denial of service, or a perception of only being a small cog in a much wider effort that will never result in them being singled out, there seems to be few inhibitors to taking protesting in to the cyber world and taking an active role in the call to action."
Just like real botnets, opt-in botnets need a command and control server from where to issue new commands, and accept status reports on the success/failure of the DDoS attack.
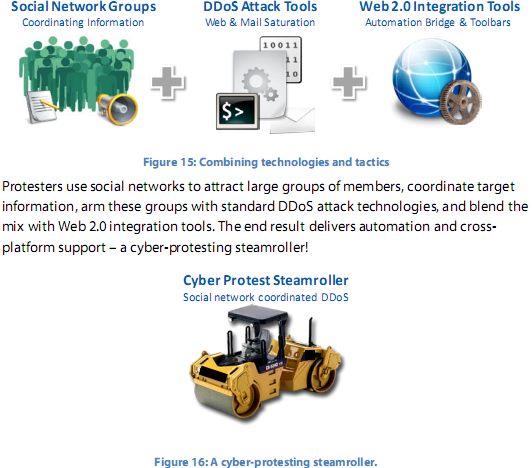
What's particularly interesting about opt-in botnets is their reliance on popular social networks such as Facebook, or micro-blogging services like Twitter, both acting as the command and control center for scheduling the attack, and distributing the attack tools.
- "Three Twitter accounts, five Yahoo! Mail accounts, twelve Google Groups, eight Blogspot blogs, nine Baidu blogs, one Google Sites and sixteen blogs on blog.com that we being used as part of the attacker’s infrastructure" - Researchers expose complex cyber espionage network
And whereas the use of legitimate networks as "virtual human shields" against potential take efforts (Twitter, Google Groups, Amazon’s EC2, Facebook as command and control servers) is nothing new, given the millions of active users and the increase ease of reaching the citizens of a particular country only, a well organized campaign could achieve its objectives by nothing else besides setting up a Facebook group, or promoting a Twitter hashtag.
Examples of Opt-in Botnets/Crowdsourcing -->
- Make Love Not Spam opt-in botnet campaign - 2004
The campaign claims to have attracted over 110,000 participants who installed their screensaver launching DDoS attacks at over 100,000 spam sites :
"Lycos Europe's approach has been cheered by some Internet users fed up with spammers' abuse of their mailbox and connectivity. The UK-based firm appears to be relying on the likelihood that the renegade sites being targeted are unlikely to use legitimate channels (such as ISP abuse departments) to report attackers. No Internet service providers have yet indicated that they will take action against subscribers participating in the attacks."
The opt-in botnet was introduced, surprisingly, by Lycos Europe who shut down the campaign on December 21, 2004 due to criticism.
- The failed Electronic Jihad (e-jihad.exe) crowdsourcing attempt - 2007
How come? Not only was their central coordination point, the official site in question shut down, but also, they have embedded a single phone back location for the application to connect back and obtain the list of the targets. Again, that was the central coordination site.
- The successful DDoS attack against CNN.com courtesy of Chinese hacktivists -2008
Next to the DDoS attack against CNN.com, this crowdsourcing attempt was perhaps among the first to utilize multiple attack tactics such as web site defacements resulting in the compromise of CNN sports to spread Pro-Chinese messages against Tibet.
"The CNN News website has twice been affected since an earlier distributed denial of service attack last Thursday. CNN fixed Thursday's attack by limiting the number of users who could access the site from specific geographical areas. Subsequently, an attack was purportedly organised to start on Saturday 19th April, but canceled.
However, our performance monitoring graph shows CNN's website suffered downtime within a 3 hour period on Sunday morning, followed by other anomalous activity on Monday morning, where response times were greatly inflated. Netcraft is continuing to monitor the CNN News website. Live uptime graphs can be viewed here."
- The Russia vs Georgia cyber attack, a combination of crowdsourcing and standard botnet - 2008
What's so impressive about their tactics? It's the convergence of PSYSOPS (psychological operations) standardized web site defacements spreading identical messages, a clear planning phrase based on the publicly distributed lists of Georgian sites susceptible to SQL injection attacks, a self-mobilization on behalf of Russian cybercriminals, and the crowdsourcing element in the face of thousands of Russians attacking Georgian sites.
Moreover, the Russian campaigners also took offline one of Georgia's most vibrant hacking forums offline in an attempt to prevent Georgian hacktivists to organize themselves.
More examples of Opt-in Botnets/Crowdsourcing -->
- The crowdsourcing cyber attack against Pro-Ahmadinejad sites - 2009
Excessive coordination took place through Twitter, in between the countless number of separate coordination sites, followed by a systematic supply of fresh proxy IPs given the censorship efforts aimed at social networking sites at the time of the attacks.
What's particularly interesting to point out about the campaign was the paradox of the "self-eating" Internet infrastructure of Iran:
"Moreover, the majority of people's information warfare driven cyber attacks we've seen during the past two years, have all been orbiting around the scenario where a foreign adversary is attacking your infrastructure from all over the world. But in the current situation, it's Iran's internal network that's self-eating itself, where the trade off for denying all the traffic would be the traffic which could be potentially influenced through PSYOPs (psychological operations)."
This disagreement over whether DDoS-ing is better than contributing user-generated content, eventually resulted in the overall decline of the DDoS efforts.
- The Pro-Israeli crowdsourcing DDoS attempt - 2009
"We created a project that unites the computer capabilities of many people around the world. Our goal is to use this power in order to disrupt our enemy's efforts to destroy the state of Israel. The more support we get, the efficient we are! You download and install the file from our site. The file is harmless to your computer and could be immediately removed. There is no need for identification of any kind - anonymity guaranteed!"
This campaign is an example of a badly executed one, with zero utilization of social media, with contributed to the quick demise of its central redirection point, and the small number of people that downloaded their software and became part of it.
Another failed crowdsourcing attempt -- in comparison their most recent attack in February, 2010 was successful -- due to the campaign's lack of social media promotion and interaction with potential users who could have opted-in.
Although the group is clearly familiar with IRC (Internet Relay Chat), Generation Y isn't, and doesn't want to.
"Operation Didgeridie consists of the distribution of DIY denial of service attack tools (404ServerNotFound.exe), launching “Fax bombs” using a GetUp! Campaign script, enticing into direct server compromise attempts by distributing a recently performed web application vulnerability assessment of Australian government web site using commercial tool."
Damballa's "The Opt-in Botnet Generation: Social Networks, Cyber Attacks, Hacktivism and Centrally-Controlled Protesting" concludes that the threats will only grow in scale and seriousness due to the ease of establishing these botnets and the ever-increasing penetration of social networks in our daily lifes.
A good question emerges from the report's conclusion - how thin is the line between being the victim, and being the enabler?
In the event of crowdsourcing driven cyber attack, would you "surrender" your bandwidth?
TalkBack.