Can Microsoft ever stop kernel tampering in Vista?

I was just going through the slides from Joanna Rutkowska's Black Hat talk (127-page .ppt file) and discovered that there's another unpatched driver flaw that exposes Windows Vista to kernel tampering.
This flaw, in NVIDIA nTune, is similar to the recent ATI Technologies driver issue that provides a foolproof way to load unsigned drivers onto Vista -- defeating one of the new security mechanisms built into Microsoft's newest operating system.
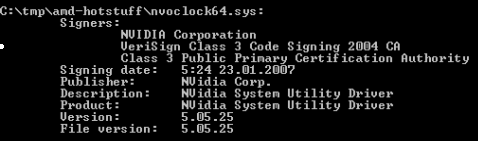
Because the buggy driver is legitimately signed, Vista will always load it, setting up a scenario where an attacker can bring the driver to the target machine, install it and then exploit it.
[ SEE: ATI driver flaw exposes Vista kernel to attackers ]
Even in cases where all device drivers are perfect (we all know that world doesn't exist), Rutkowska showed how certificates can be purchased by anyone for $250 and attached to legitimate drivers rigged with what she calls "innocent" backdoors.
"Nobody can charge us for creating and signing an 'innocent' driver, which just happens to be somewhat buggy (a subtle buffer overflow somewhere," she argues. The driver can then be loaded into Vista (legitimately) and the attacker can simply exploit the bug to get access to the kernel.
"It's not our driver that behaves maliciously, but it's the exploit, which is not signed by any certificate."
The takeaway from Rutkowska's talk, which is not being disputed by Microsoft, is that it's not possible to implement effective kernel protection using device driver signing.
Alex Ionescu's Purple Pill, which piggy-backed on the ATI driver flaw, put Rutkowska's theory into practice and sent Redmond scurrying to look at its anti-rootkit/anti-DRM security mechanisms.
Last Tuesday, as part of Patch Day, Microsoft shipped a non-security update (see advisory here) to add additional checks to the Kernel Patch Protection system. This update, which was NOT related to the Purple Pill release, is meant to protect code and critical structures in the Windows kernel from modification by unknown code or data.
I exchanged e-mails with Ken 'Skywing' Johnson, a Microsoft SDK MVP known for breaking Vista's PatchGuard, and he explained the latest update as just another salvo in the never-ending cat-and-mouse game to attack -- and defend -- the Windows kernel.
"It changes t he way that PatchGuard's integrity checks are periodically run in an effort to break publicly available code that disabled PatchGuard v2. This includes the code that I published for disabling PatchGuard v2 in Uninformed vol 6," Johnson said.
It also extends PatchGuard's integrity check to include several other key areas that could possibly be used to achieve results similar to patching the kernel but without arousing PatchGuard's attention (which would allow one to simply ignore PatchGuard entirely and coexist with it while still altering the behavior of the kernel in ways that PatchGuard was designed to stop).
In other words, Johnson explained, it's the latest iteration in the play-by-play between Microsoft and anybody who wants to patch the kernel. "As far as I know, it is successful in stopping all of the current, publicly available code for disabling PatchGuard v2. However, a motivated and skilled individual would likely not find the new PatchGuard version unstoppable," he added.
"Microsoft is fighting a primarily reactive battle against people who are (or might be) shipping code that is designed to disable PatchGuard... I would consider it very likely that the new revision will be disabled just as effectively as v2 and v1 have, given time," Johnson argued.
For its part, Microsoft views Kernel Patch Protection and the device driver signing mechanism as "parts of a defense in depth approach to security. "
A spokesman explained to me that PatchGuard and practices such as using User Account Control (which limits how much code runs with administrative permissions) are parts of this approach that combine to make the operating system hacker-proof.
"Windows Vista was engineered to be the most secure version of Windows, however it is important to note that no operating system is 100% secure. Microsoft periodically reviews and adjusts mechanisms such as KPP based on evolving research and threads – security is an ever evolving process," he added.