Copyright violation alert ransomware in the wild
UPDATED: Wednesday, April 28, 2010: How to remove the ICPP Copyright Violation Alert ransomware
A currently ongoing ransomware campaign is using a novel approach to extort money from end users whose PCs have been locked down.
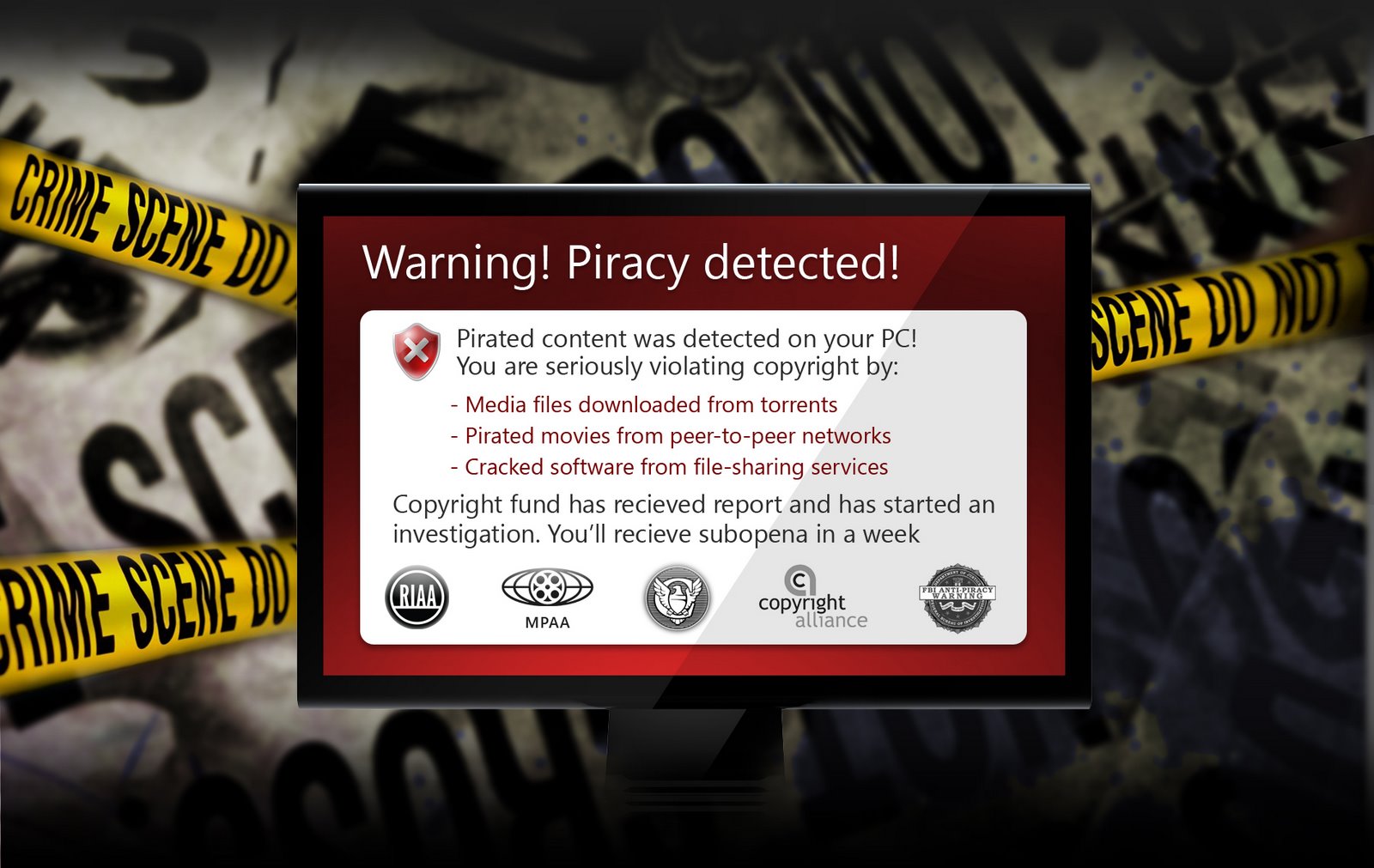
By pretending to be the fake ICPP Foundation (icpp-online.com), the ransomware locks down the user's desktop issuing a "Copyright violation: copyrighted content detected" message, which lists torrent files found on the infected PC, and forces the user to pay $400 for the copyright holder's fine, emphasizing on the fact that "the maximum penalties can be five years in prison and up to $250,000 in fines.
More details on the campaign:
Upon execution the ransomware will change the Desktop's wallpaper to the "Warning! Piracy detected!" background.
- Consider going through the The Ultimate Guide to Scareware Protection to find out more about how malware/scareware and ransomware propagates, and how to avoid falling victim into the scam
It will then make sure the warnings appear every time the end user restarts PCs. In between, it will lock down the end user's Desktop, featuring the "Copyright violation: copyrighted content detected" window:
The window attempts to trick the end user into believing that:
- "Windows has detected that you are using content that was downloaded in violation of the copyright of its respective owners. Please read the following bulletin and try solving the problem in one of the recommended ways. During the system scan Antipiracy foundation scanner has detected copyright issues. Please take a look at the list and choose an action: pass the case to a court or settle it in pre-trial order by paying a fine."
Attempts to get rid of it result in the following message:
- "Performing this action is construed as refusal to cooperate with the copyright holder and unwillingness to consider pre-trial settlement. If you continue, all the data gathered will be passes to copyright protection organizations and to the court. We recommend cancelling this action and choosing the option "pre-trial settlement"."
Gullible end users who fall victim to the scam, will then be asked to pay $399.85 for a "Legal license purchase", "Copyright holder fine", a "Copyright protection organization fee for the use of software tracking illegal file downloads" and a "Traffic fee".
Basically, you've got a profit margin driven ransomware business model, that's ironically charging you a fee for the development of ransomware "software" itself. The cybercriminals behind the campaign are also aware of the concept of localization. The ransomware will adapt to each user's PC, and issue the same messages in 10 different languages - Czech, Danish, Dutch, English, French, German, Italian, Portuguese, Slovak and Spanish.
- UPDATED: Find out more about this campaign's connections with related ZeuS crimeware, and money mule recruitment campaigns
- UPDATED2: Basic malware/scareware/ransomware prevention tips for Windows users.
The ransomware is currently detected as Win32/Adware.Antipiracy and Rogue:W32/DotTorrent.A.