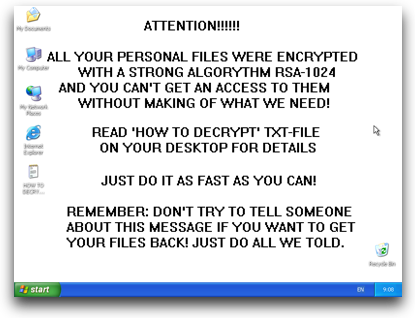
GpCode ransomware returns, with stronger encryption

A new version of the dangerous GpCode ransomware has been detected, using RSA-1024 and AES-256 as crypto-algorithms.
According to Vitaly Kamluk of Kaspersky Lab (disclosure: my employer), the latest iteration of this malware is stronger than ever.
GpCode is back and it is stronger than before. Unlike the previous variants, it doesn't delete files after encryption. Instead it overwrites data in the files, which makes it impossible to use data-recovery software such as PhotoRec, which we suggested during the last attack.
Kamluk offers some advice for any Windows user that sees this ransom warning after an infection:
If you think you are infected, we recommend that you do not change anything on their systems as it may prevent potential data recovery if we find a solution. It is safe to shutdown the computer or restart it despite claims by the malware writer that files are deleted after N days - we haven't seen any evidence of time-based file deleting mechanism. But nevertheless, it is better to stay away from any changes that could be made to the file system which, for example, may be caused by computer restart.
People who are not should be aware of the problem and should recognize GpCode from the first second when the warnings appears on your screen. Pushing Reset/Power button on your desktop may save a significant amount of your valuable data!
ALSO SEE: