GPU-Accelerated Wi-Fi password cracking goes mainstream
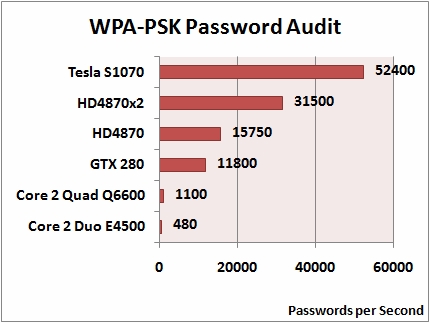
What's particularly interesting about the Wireless Security Auditor is that it attempts to accomplish the password recovery in an offline/stealth mode, instead of the noisy direct router brute forcing approach :
"Elcomsoft Wireless Security Auditor works completely in off-line, undetectable by the Wi-Fi network being probed, by analyzing a dump of network communications in order to attempt to retrieve the original WPA/WPA2-PSK passwords in plain text. Elcomsoft Wireless Security Auditor requires a valid log of wireless communications in standard tcpdumptcpdump. The tcpdumptcpdump format is supported by all commercial Wi-Fi sniffers. In order to audit your wireless network, at least one handshake packet must be present in the tcpdump file."
Meanwhile, pen-testing companies have once again urged IT managers and end users to go beyond the 8 character password strength myth, and anticipate the risks posed by the increasingly efficient password recovery solutions hitting the market :
"David Hobson said: “It's a wake-up call to IT managers, pure and simple. IT managers should now move to 12 and even 16 character keys as a matter of urgency. It's not very user-friendly, but the potential consequences of staying with eight character keys do not bear thinking about."
As previously discussed, best practices wake-up calls remains largely ignored prompting radical solutions in countries like India for instance, which recently announced that a Wardriving police unit will be locating insecure wireless networks and notifying the owners in order to "prevent the commission of a cognizable offense".