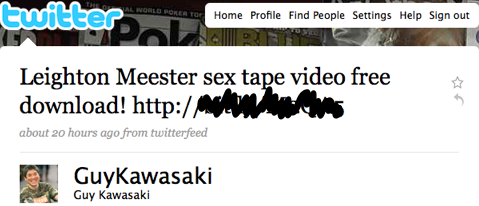
Guy Kawasaki's Twitter account hijacked, pushes Windows and Mac malware

The Twitter account belonging to venture capitalist and Mac evangelist Guy Kawasaki was hijacked yesterday and used to push malware to some 140,000 Twitter users. The attack (screenshot above) included a link to what purported to be a "sex tape video free download" linked to Gossip Girls star Leighton Meester but, after a series of clicks, the end result was a malicious Trojan.
[ SEE: Coming in July: Month of Twitter Bugs ]
Kawasaki would later apologize but, as Trend Micro's Rik Ferguson explains, the damage was significant for any of his tens of thousands of followers.
In this case, following the link would be a Very Bad Idea because it will lead you to a malicious website designed to infect both Macs and PCs with a DNS changing Trojan which at the time of writing has low-to non-existent detection rates by security vendors...
On Windows machines, a user falling for the bait gets to a series of Web pages featuring pornographic content and, at the end, a prompt to update a video codec. That fake codec is a piece of malware.
On the Mac platform, Intego reports that the download is a disk image called ActiveXsetup.dmg. Here's the end result:
This Trojan horse, a form of DNSChanger, uses a sophisticated method, via the scutil command, to change the Mac’s DNS server (the server that is used to look up the correspondences between domain names and IP addresses for web sites and other Internet services). When this new, malicious, DNS server is active, it hijacks some web requests, leading users to phishing web sites (for sites such as Ebay, PayPal and some banks), or simply to web pages displaying ads for other pornographic web sites. In the first case, users may think they are on legitimate sites and enter a user name and password, a credit card, or an account number, which will then be hijacked. In the latter case, it seems that this is being done solely to generate ad revenue.
It is not yet known how Kawasaki's Twitter account got compromised but there is speculation is security circles that he fell victim to a Twitter phishing attack that swiped his password.
It is clear that Twitter's popularity is now at the stage where it is ripe for these types of targeted attacks.