Hackers hijack DNS records of high profile New Zealand sites
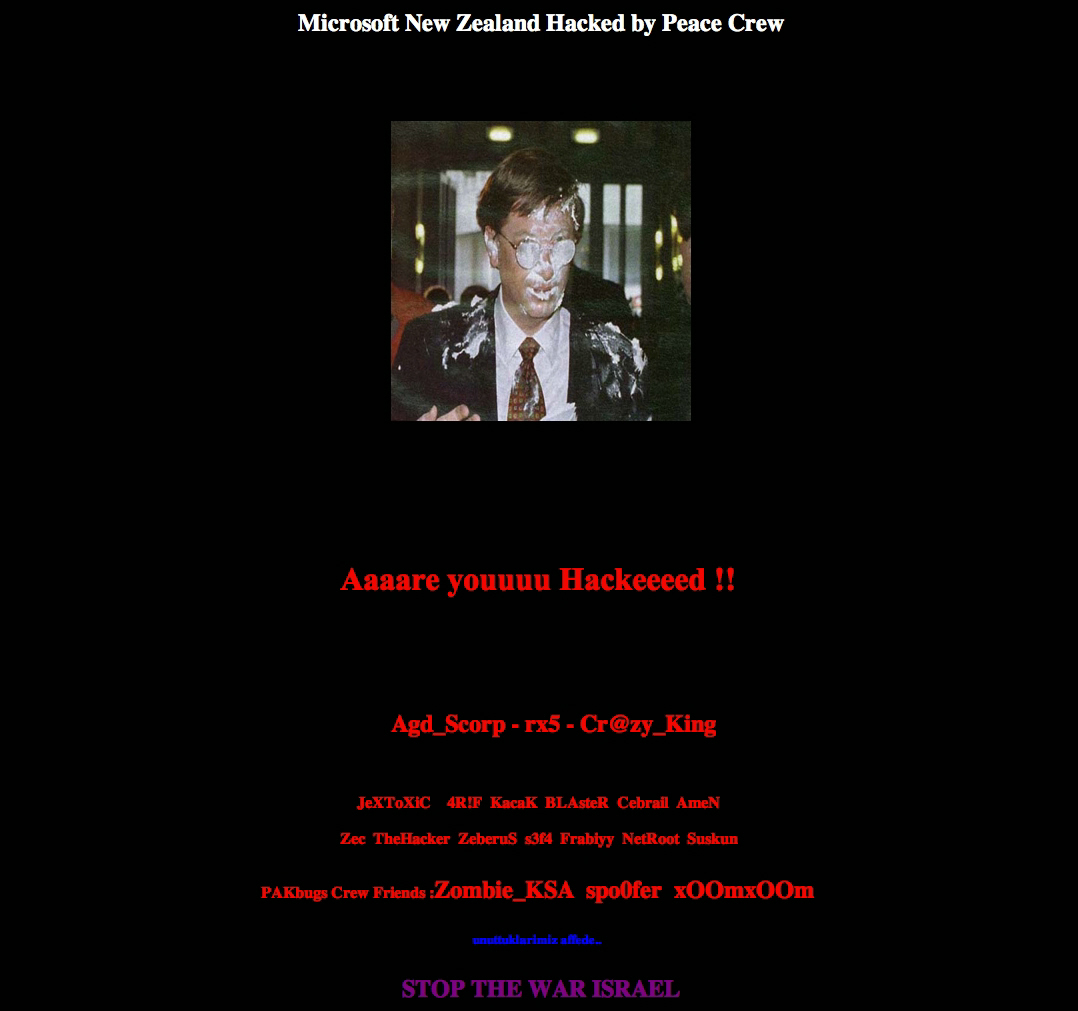
Today, a web site defacement group known as "The Peace Crew" has successfully hijacked the DNS records for high profile New Zealand web sites, through what Zone-H claims to be a SQL injection at New Zealand's based registrar Domainz.net, in order to redirect the visitors to a defaced page featuring the infamous Bill Gates pieing photo, as well as anti-war messages.
The mass defacement affected major Microsoft sites in New Zealand including WindowsLive.co.nz, MSN.co.nz, Microsoft.co.nz, Hotmail.co.nz, Live.co.nz next to HSBC.co.nz, Sony.co.nz, Coca-Cola.co.nz, Xerox.co.nz, Fanta.co.nz, F-Secure.co.nz and BitDefender.co.nz.
Here's Microsoft's comment:
"MSN have responded by issuing a short statement from MSN business manager Liz Fraser this afternoon. "The cause of this discrepancy has been identified and we are currently working with our Microsoft technology and security teams in the US to resolve the matter as quickly as possible today. "We apologise for any inconvenience this may have caused," the statement said."
Once control to the domain registrar's web panel was obtained, members of the Peace Crew used fatih1.turkguvenligi .info and fatih2.turkguvenligi .info as primary DNS servers delivering the defaced pages, and making it look like the sites themselves have been compromised.
- Go through related hacktivism/web site defacement cases: Thousands of Israeli web sites under attack; Pro-Serbian hacktivists attacking Albanian web sites; Hundreds of Dutch web sites hacked by Islamic hackers; 300 Lithuanian sites hacked by Russian hackers; Chinese hackers deface the Russian Consulate in Shanghai; China detains web site defacer spreading earthquake rumors
The group is not new on the defacement scene, in fact one of its members has been keeping himself pretty busy during this month by having already defaced thirteen web servers belonging to NASA, using the same template.