Mac botnet generated $10,000 a day for Flashback gang

Security researchers at Symantec are estimating that the cyber-crimibals behind the Flashback Mac OS X botnet may have raked in about $10,000 a day.
In a new blog post that discusses the business model of the botnet, Symantec found that Flashback was robbing Google of advertising dollars by redirecting clicks from infected Mac OS X machines and stealing the ad revenue.
At its height, Flashback contained more than 700,000 Mac machines and Symantec calculates that a botnet of that size could easily generate about $10,000 a day in click-fraud.
Some details from Symantec's blog:
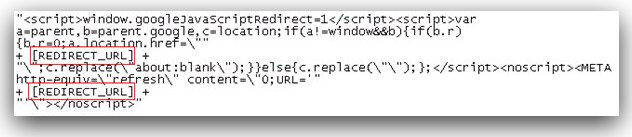
The Flashback ad-clicking component is loaded into Chrome, Firefox, and Safari where it can intercept all GET and POST requests from the browser. Flashback specifically targets search queries made on Google and, depending on the search query, may redirect users to another page of the attacker's choosing, where they receive revenue from the click . (Google never receives the intended ad click.)
The ad click component parses out requests resulting from an ad click on Google Search and determines if it is on a whitelist. If not, it forwards the request to [a] malicious server.
Symantec reports that the hijacked ad click is based on a user searching for "toys".
We can clearly see a value of 0.8 cents for the click and the redirection... This redirected URL is subsequently written into the browser so that the user is now directed to the new site, in effect hijacking the ad click Google should have received.
"This ultimately results in lost revenue for Google and untold sums of money for the Flashback gang," Symantec said.