McAfee debunks recent vulnerabilities in AV software research, n.runs restates its position
"A recent ZDnet blog discusses a large number of vulnerabilities German research team N.Runs says it found in antimalware products from nearly every vendor. The ZDNet posting includes scary graphs to frighten users of security products. We researched the N.Runs claims by analyzing the raw data and found their claims to be somewhat exaggerated. We will discuss our findings (and make available our source data) in the attached document. We have also provided our source data for anyone who wishes to examine it."
Today, n.runs AG has issued a response to McAfee's statement, providing even more insights into the vulnerabilities they've managed to find, how they found them, and why are the affected antivirus vendors questioning the number of flaws in general :
"n.runs recently announced that they discovered over 800 vulnerabilities in AV software, blaming a necessary procedure that is known as parsing. These flaws potential give attackers access to sensible Data. McAfee reacted by posting a statement to the McAfee Avert blog, n.runs would hereby like to take the opportunity and react to these statements.
As a reaction McAfee posted an statement to their Avert blog, which tries to negate some of the statements given in the original n.runs Press-release, this represents a short summary of our response to the McAfee Statement on AV Vulnerabilities. For the complete response see: Response to McAfee Statement (PDF)"
In order to provide a more informal overview of the big picture, the conflict of interest, as well as the current situation, I took a brief interview with Thierry Zoller which you can find below.
Constructive confrontation, namely, "you're always wrong with the idea to come up with a better solution", ultimately better serves the customer. Moreover, in regard to vulnerabilities found in antivirus software, you have to consider the following - which vulnerability is in fact more dangerous, the one leading to remote code execution through an antivirus scanner, or one that is bypassing the scanning process of the software allowing malware to easily sneak in?
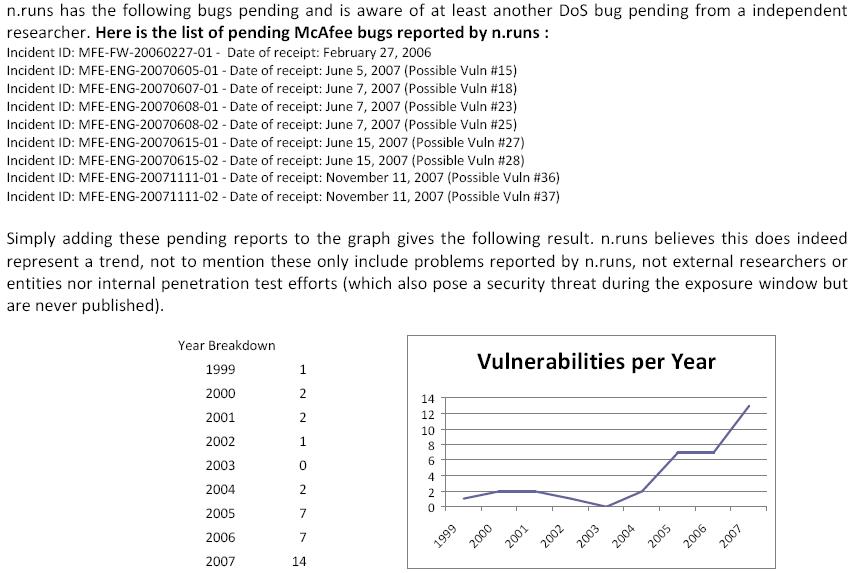
Following n.runs research into the topic for a while now, copies of their presentations presented at last year's Chaos Comunication Camp (Antivirus (In)Security) and this year's CanSecWest (The Death of AV Defense in Depth?- revisiting Anti-Virus Software) their KISS strategy in a combination with the universal way in which antivirus software works, is prone to come up with relevant results. Here are Zoller's comments :
Dancho : What was the first thing that came to your mind when you saw the statement issued by McAfee, and do you think there's a difference between a scared, a concerned, and objectively informed customer of a security product?
Thierry : I welcome any reaction on the part of AV Vendors, in some cases however I truly believe customers should be scared. Especially those with AV software running directly on their MTA or Email server. In this particular case, I think there is a difference between scared and objectively informed, one follows the other. You can guess in what order.
Dancho : What's more disturbing in general, the average time it takes to patch a reported vulnerability within an AV, or the average time it takes to actually receive a response acknowledging the flaw at the first place?
Thierry : This really depends on the vendor and the designated security contact @ the vendor. Some vendors choose to have development directly answer security notices, as these persons regard their code as their baby it's often hard to convince them and you sometimes have to sustain quite some abuse - and negation. Sometimes there is simply no other way than to hit them with a working PoC in the face.
Some put a Product managers in front, some technical account managers, it really depends on how well these persons are informed about the procedure to follow. There are vendors that send you a summary update of the progress every week, and some you have to send 5 followup emails to get the status.
The most disturbing part is the amount of work required to explain flaws and the lacking knowledge on how to coordinate patching. Some vendors patch silently and don't even tell you, then claim (after x months) that the bug was found internally, some vendors don't publicly announce that a patch fixed bugs of security relevance. And this really sucks. You see we put a lot of effort in coordinating disclosure, but when you deal with 13 av vendors and one of them takes 2 years, well you have to wait 2 years until you announce the advisory. For a flaw that took other vendors 10 days to patch...
In some cases I had to fight with support guys asking for serial numbers or else they would not "help" me, telling them you are doing them a favor by reporting security issues - was, let's say - not really understood. Some vendors don't even have a security@ or secure@ address, and it took us around 8 month to find the correct address to report the issues to, and this for a well known vendor.
Dancho : How would you describe the actual applicability of the vulnerabilities n.runs found in antivirus products, namely are they the type of vulnerabilities "that could" or are in fact vulnerabilities "that currently are", and what's your take on not taking action until an incident abusing these vulnerabilities takes place, a event worth dedicating a patch for?
Thierry : All of the bugs we reported are verified before submission, the attitude of not taking action until damage is being seen ("being done" is not enough since they are not aware of) is jeopardizing the security and trust of their clients. But it's quite common in the AV industry - reacting to outbreaks, reacting to malware. Reaction; I was quite baffled that the argument "hey we wait until that flaw is publicly exploited" actually still exists. Every bug that posed a risk over a certain timeframe should be communicated to clients :
- Flaws found by external researchers - Flaws found by internal auditors (at least the critical ones)
Otherwise you'll leave it to those that 'bindiff' your patches and customers at risk. I understand that these things ofter create friction with PR/Marketing department.
Dancho : Can we speak of "window of opportunity" regarding these vulnerabilities, or perhaps we should say "the wide open window of opportunity with big blinking letters saying come on in" in respect to the slow response and coordination, excluding the fact that some of flaws aren't even acknowledged as such yet?
Thierry : As long as a vulnerability is not patched, it's possible that someone else is actively exploiting it. That said, a window of opportunity certainly exists. The same is true for bugs found internally in deployed software.
Dancho : If you were among the affected parties it this research, what would you do to ensure that your customers are protected from flaws within a software that's supposed to protect them in general? Moreover, what should the end user keep in mind when choosing an antivirus product if you were to generalize your advice?
Thierry : I would rather not comment on this, I am non neutral in this one. A home user is rarely the target of a sophisticated 0day attacks, as such he should choose the AV software that suits him mixed with detection rates. However Enterprises should hold vendors accountable, ask for more details.
Dancho : Isn't the single most important vulnerability found in antivirus software during the last couple of years, the easy to bypass signatures based scanning approach, and the product concept myopia of spending years of research into heuristics where the same amount of resources should have probably been spend on behavioral detection solutions?
Thierry : From a larger viewpoint, concentrating the functional aspect of AV software - you are absolutely correct. The "problem" with behavioral detection is this one - they need less updates and..updates is what keeps the AV business model rolling. If this would have not been the case - I am sure we would have a lot better behavioral and overall detection nowadays. It's ridicule how easy it is to bypass heuristics.
Conflict of interests are common for every industry, however, it shouldn't be the end user the one provided with a false feeling of security, by not reminding him that security software is also vulnerable to security flaws, for the sake of helping him make a more informed strategic decision when purchasing such solutions. Moreover, relying on a perimeter defense security solution in the face of a single antivirus software is precisely what Defense-in-Depth isn't all about.