Metasploit Project's site hijacked through ARP poisoning
Metasploit, the open-source platform for developing, testing, and using exploit code, got its official project site briefly hijacked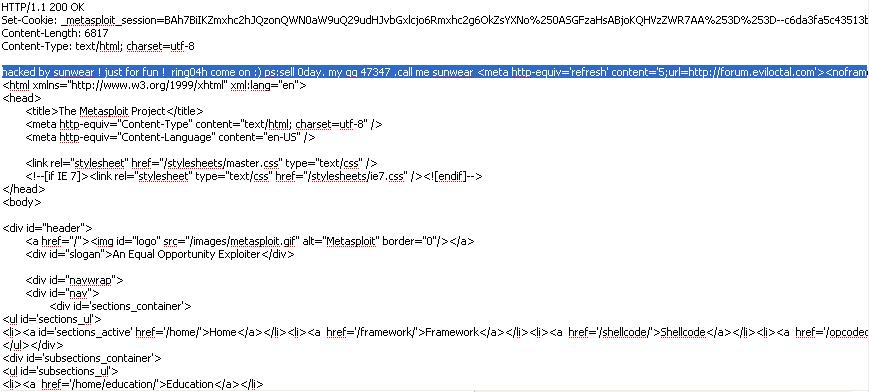
"Problem solved. Someone is ARP poisoning the IP address of the router on which the www.metasploit.com server resides. I hardcoded an ARP entry for the real router and that seems to solve the MITM issue. It doesn't help the other 250 servers on that network, but thats an issue for the ISP to resolve."
The Chinese hackers then distributed an image of what Metasploit.com looked like in the time of the ARP poisoning on the forum where the site used to redirect its visitors to, as you can also see for yourself. Offering to sale a zero day exploit by hijacking Metasploit's official site is surreal enough not to consider the possibility that a real zero day exploit could have been served if they were to fully abuse the man-in-the-middle attack potential.