Microsoft warns: Expect exploits for critical Windows worm hole

Attention Microsoft Windows administrators: Stop what you're doing and apply the new -- and very critical -- MS12-020 update.
Microsoft is warning that there's a remote, pre-authentication, network-accessible code execution vulnerability in its implementation of the RDP protocol.
From the bulletin:
A remote code execution vulnerability exists in the way that the Remote Desktop Protocol accesses an object in memory that has been improperly initialized or has been deleted. An attacker who successfully exploited this vulnerability could run abitrary code on the target system. An attacker could then install programs; view,change, or delete data; or create new accounts with full user rights.
The vulnerability, which affects all versions of Windows, was privately reported to Microsoft's via the ZDI vulnerability broker service and the company said it was not yet aware of any attacks in the wild.
Although RDP is disabled by default, Microsoft is urging all Window users to treat this issue with the utmost priority.
"Due to the attractiveness of this vulnerability to attackers, we anticipate that an exploit for code execution will be developed in the next 30 days," Microsoft said.
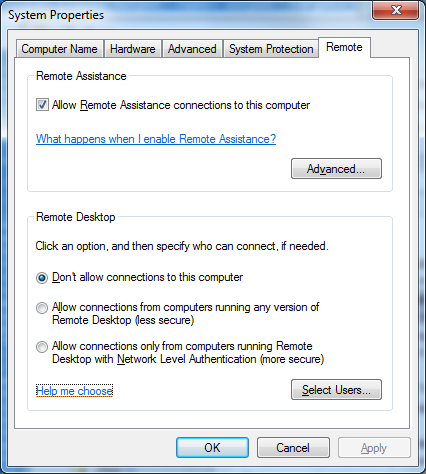
It's important to note that the vulnerable code is reachable only if RDP is enabled and a mitigation feature in RDP called NLA (network level authentication) moves it to post-authentication which makes this vulnerability less likely to be wormed. There are instructions here to enable NLA on Windows to reduce the severity of a potential attack.
[ SEE: Ten little things to secure your online presence ]
The Remote Assistance feature in Windows (see image above) provides checkboxes for users to choose between “more secure” and “less secure”. On machines where RDP is enabled in the “less secure" mode, nothing blocks pre-auth code execution once a stable exploit is developed.This issue is potentially reachable over the network by an attacker before authentication is required. RDP is commonly allowed through firewalls due to its utility. The service runs in kernel-mode as SYSTEM by default on nearly all platforms (except for one exception described below). During our investigation, we determined that this vulnerability is directly exploitable for code execution. Developing a working exploit will not be trivial – we would be surprised to see one developed in the next few days. However, we expect to see working exploit code developed within the next 30 days.
In all, Microsoft shipped six security bulletins as part of this month's Patch Tuesday batch. The updates address seven documented vulnerabilities in Microsoft Windows, Visual Studio and Expression Design.