Open source software security improving
You cannot say something's good or bad unless you benchmark or compare it against something else. According to the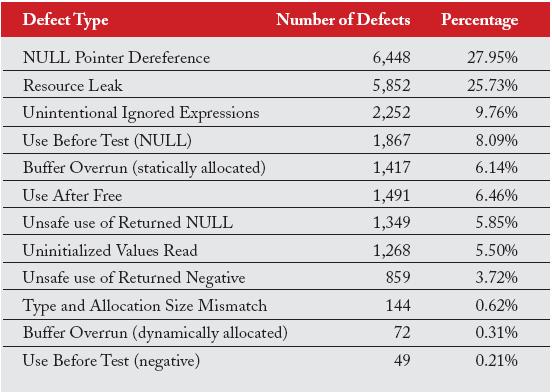
Key summary findings of the report :
Findings are based on analysis of over 55 million lines of code on a recurring basis from more than 250 open source projects, representing 14,238 individual project analysis runs for a total of nearly 10 billion lines of code analyzed. In summary, this report contains the following findings:
- The overall quality and security of open source software is improving – Researchers at the Scan site observed a 16% reduction in static analysis defect density over the past two years
- Prevalence of individual defect types – There is a clear distinction between common and uncommon defect types across open source projects
- Code base size and static analysis defect count – Research found a strong, linear relationship between these two variables
- Function length and static analysis defect density – Research indicates static analysis defect density and function length are statistically uncorrelated
- Cyclomatic complexity and Halstead effort – Research indicates these two measures of code complexity are significantly correlated to codebase size
- False positive results – To date, the rate of false positives identified in the Scan databases averages below 14%
The most prevalent defect found in the study was the null-pointer dereference representing 27.95% of all defects, followed by resource leak, and the most commonly known buffer overflows comprising only 6% of the total issues identified. Perhaps the most valuable benefit out of the whole project is the fact that insecure coding practices would be easily spotted, and more awareness build on how to prevent this from happening. Consider going through the report, and include your open source software in the Scan project.