Over 600,000 Macs infected with Flashback Trojan

Update - Apple developing tool to detect and remove Flashback Trojan
Two months ago, a new variant of the Flashback Trojan started exploiting a security hole in Java to silently infect Mac OS X machines. Apple has since patched Java, but this was only yesterday. As of today, more than 600,000 Macs are currently infected with the Flashback Trojan, which steals your user names and passwords to popular websites by monitoring your network traffic.
Russian antivirus company Dr. Web first reported today that 550,000 Macs were being controlled by the growing Mac botnet. Later in the day though, Dr. Web malware analyst Sorokin Ivan announced on Twitter (via Ars Technica) that the number of Macs infected with Flashback had increased to over 600,000:
@mikko, at this moment botnet Flashback over 600k, include 274 bots from Cupertino and special for you Mikko - 285 from Finland
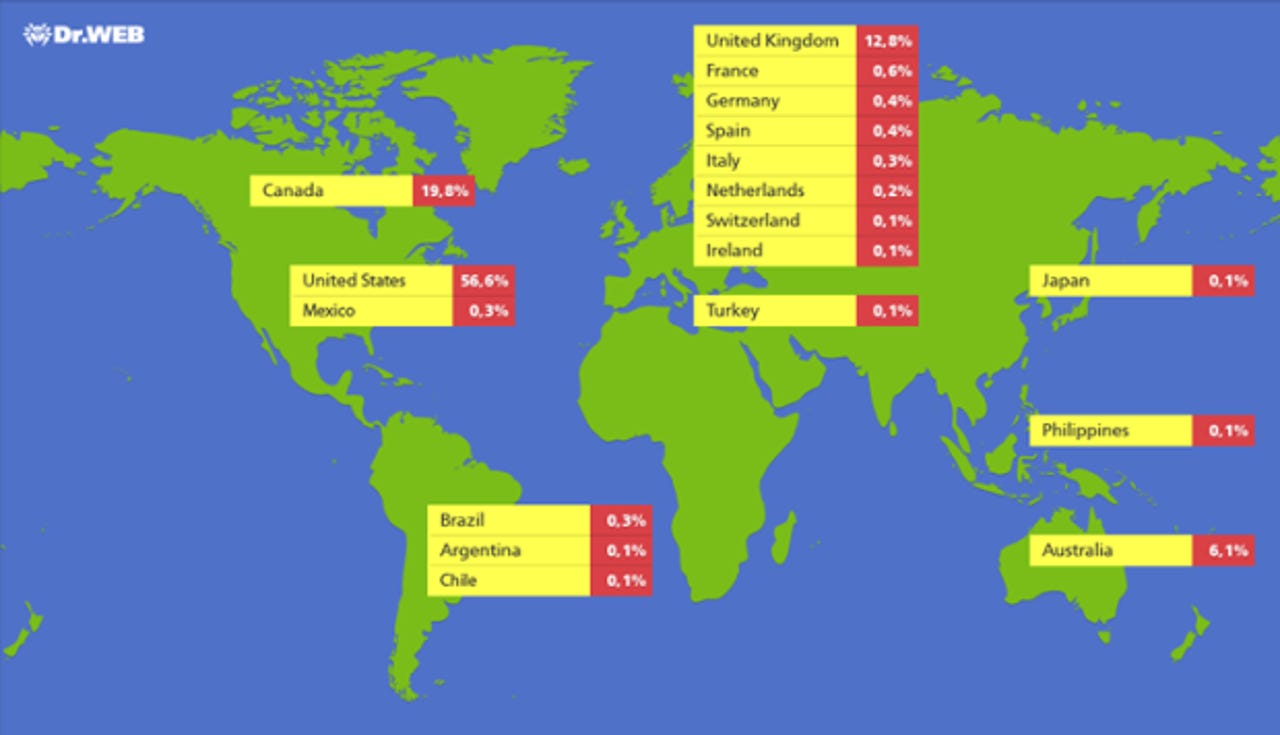
As you can see in the screenshot above, Dr. Web says 56.6 percent of the infected Macs are located in the U.S., 19.8 percent are in Canada, and 12.8 percent are in the U.K.
Flashback was initially discovered in September 2011 masquerading as a fake Adobe Flash Player installer. A month later, a variant that disables Mac OS X antivirus signatures updates was spotted in the wild.
In the past few months, Flashback has evolved to exploiting Java vulnerabilities. This means it doesn't require any user intervention if Java has not been patched on your Mac: all you have to do is visit a malicious website, and the malware will be automatically downloaded and installed.
Another variant spotted last month asks for administrative privileges, but it does not require them. If you give it permission, it will install itself into the Applications folder where it will silently hook itself into Firefox and Safari, and launch whenever you open one of the two browsers. If you don't give it permission, it will install itself to the user accounts folder, where it can run in a more global manner, launching itself whenever any application is launched, but where it can also more easily detected.
You can grab the new version of Java that patches the security hole in question from Apple here: Java for Mac OS X 10.6 Update 7 and Java for OS X Lion 2012-001. Additionally, F-Secure has instructions on how to remove this malware if you think your Mac may already be infected.
Update - Apple developing tool to detect and remove Flashback Trojan
See also:
- Flashback Mac OS X malware exploiting (old) Java security holes
- New Mac OS X malware variant spotted in the wild
- New Mac OS X trojan spotted in the wild
- New Mac OS X malware disables Apple's malware protection
- Apple blocks malware-as-PDF threat but new attack emerges
- Have you uninstalled Java yet? Here are 14 new reasons...