Patch Tuesday heads-up: 8 bulletins, 5 critical

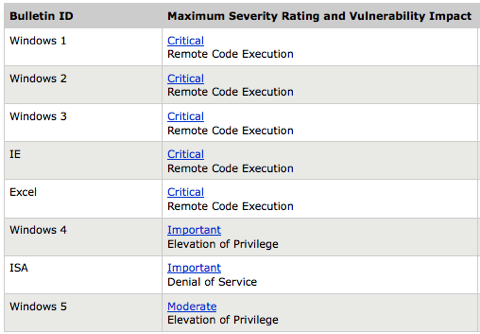
Microsoft plans to ship 8 security bulletins next Tuesday (April 14, 2009) to fix remote code execution and denial of service vulnerabilities affecting Windows, Office and Internet Explorer.
According to the company's Patch Tuesday advance notice, five of the bulletins will be rated "critical," meaning they can be exploited by hackers to take complete control of Windows machines.
[ SEE: Microsoft issues Safari-to-IE blended threat warning ]
I've been given a heads-up that one of the Internet Explorer vulnerabilities being fixed is the musty old Safari-to-IE carpet bombing blended threat that combined flaws in two browsers into a code execution attack.
The IE flaw was originally discovered and reported by Aviv Raff back in November 2006 (more than two years ago!) but was ignored by Microsoft until the Safari carpet-bombing bug emerged to show how a combo-attack could lead to complete PC takeover.
[ SEE: Why Apple must fix Safari 'carpet bombing' flaw immediately ]
I'm told Microsoft will actually issue two separate bulletins on this issue -- one with a patch that changes several calls to LoadLibrary and SearchPath in Internet Explorer to stop the browser from attempting to load libraries directly from the desktop.
Microsoft will also push out additional defense-in-depth protections and a new API to further limit the damage from hacker attacks but because of application compatibility issues, the protections will NOT be enabled by default.
In addition to the high-priority IE bulletin, next Tuesday's patch batch will include five different Windows bulletins (four rated critical), a solitary Microsoft Excel update (critical), and an ISA denial-of-service issue that Microsoft rates as "important."