Report: 3 million malvertising impressions served per day
According to data released by Dasient, the company observed a 100 percent increase in malvertising attacks from Q3 to Q4 2010, from 1.5 million malvertising impressions per day in Q3 2010 to 3 million malicious impressions in Q4.
Some highlights from the report:
- The average lifetime of a malvertising campaign has dropped for the second consecutive quarter in a row -- down to an average of 9.8 days, as compared to 11.1 in Q3, and 11.8 in Q2.
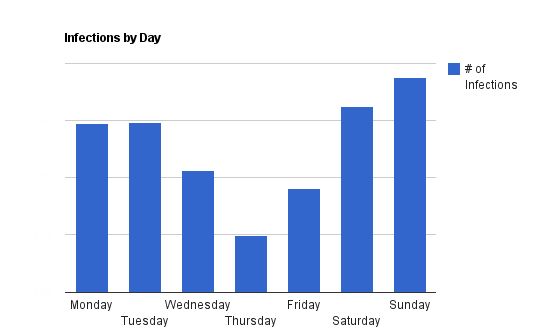
- Malvertisers typically mount their attacks on weekends, during which IT departments are slower to respond, as we have seen in previous quarters, and continued to see in Q4 2010 as per the figure below.
- Over the past year, we’ve estimated that over 4 millions domains have been infected.
- After three months of web browsing, the probability that an average Internet user will hit an infected page is approximately 95%.
It's the higher click-through rate achieved that matters, with the ads appearing on trusted and high trafficked web sites. In some cases, the click-through rate from even a short-lived campaign can outpace, the click-through rate from a well coordinate blackhat SEO (search engine optimization) campaign.
According to Dasient, the malicious attackers usually rely on remnant advertising, that is advertising inventory which isn't sold until the last minute, and work typically on the weekends, with the idea to increase the average time it would take for an IT department to take down the malvertising campaign. Similar studies conducted by Google indicate that the most typical content served is fake security software also known as scareware.
Users are advised to browse the Web in a sandboxed environment, using least privilege accounts, NoScript for Firefox, and ensuring that they are free of client-side exploitable flaws.