Research: Small DIY botnets prevalent in enterprise networks
Contrary to the “common wisdom” that based on their size, big botnets are theoretically capable of infiltrating a huge percentage of enterprise networks, a recently presented study entitled "My Bots Are Not Yours! A case study of 600+ real-world living botnets" shows an entirely different picture.
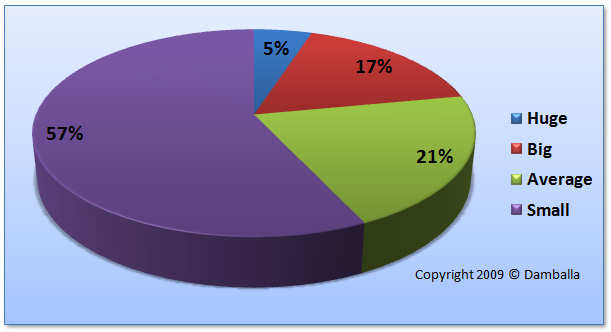
According to Gunter Ollmann, VP of research at Damballa, based on their observation of 600 different botnets within global enterprises throughout a period of three months, small DIY botnets aiming to stay beneath the radar accounted for 57% of all botnets, and hence, successfully evaded detection in most of the cases:
"The average size of the 600 botnets we examined hovered in the 101-500 range on a daily basis. Why do I use the term “on a daily basis”? Because the number of active members within each botnet tend to change daily – based upon factors such as whether the compromised hosts were turned on or part of the enterprise network (e.g. laptops), whether or not they had been remediated, and whether or not the remote botnet master was interactively controlling them.
While many people focus on the biggest botnets circulating around the Internet, it appears that the smaller botnets are not only more prevalent within real-life enterprise environments, but that they’re also doing different things. And, in most cases, those “different things” are more dangerous since they’re more specific to the enterprise environment they’re operating within."
For instance, in 2007, researchers from Support Intelligence launched an initiative called "30 Days of Bots" aiming to highlight Fortune 1000 businesses sending out spam through malware infected hosts within their networks. Their initiative provided interesting results, emphasizing on the modest number of infected hosts found within the following companies:
- 3M; Thomson Financial; AIG; Aflac, Inc; BusinessWeek; Toshiba America Business Solutions; Conseco; Bank of America Securities; Clear Channel; Borders Group; Affiliated Computer Services; Nationwide Insurance; ATA Airlines; Intel; and IndymacBank
What the researchers from Support Intelligence did, is something cybecriminals have been doing and offering as a service for a while - data mining, or from their perspective, the ability to data mine a big botnet and rent access to hosts residing on particular networks not for the purpose of spam sending, but for targeted corporate espionage.
According to the just released MessageLabs Intelligence report for August, the Grum and Bobax botnets have overtaken the leading position of Cutwail/Pushdo, currently responsible for 23.2% and 15.7% of all spam respectively, with an estimated botnet size for Grum at 560k to 840k followed by Bobax with 80k to 120k infected IPs.