Researchers peek inside a mini ZeuS botnet, find 60GB of stolen data
Just how much data can be harvested from 55,000+ crimeware-infected hosts?
According to a newly published report by AVG, upon obtaining access to a mini ZeuS botnet dubbed Mumba, part of Avalanche group's online operations, they found 60GB of stolen data such as, accounting details for social networking sites, banking accounts, credit card numbers and intercepted emails.
"Detected by AVG security products, the “Mumba” botnet was found to be using four different variations of the latest version of the Zeus malware to steal data from compromised machines. Zeus version 2.0.4.2 now supports the latest Microsoft operating system – Windows 7, and is able to steal HTTP traffic data from the Mozilla Firefox browser.
The “Mumba” botnet, which makes use of the prolific Zeus malware, has compromised more than 60GB of data from approximately 55,000 users’ PCs around the world. The data includes user credentials of social networking Web sites, banking accounts, credit card numbers, email communications and more. "
Key points:
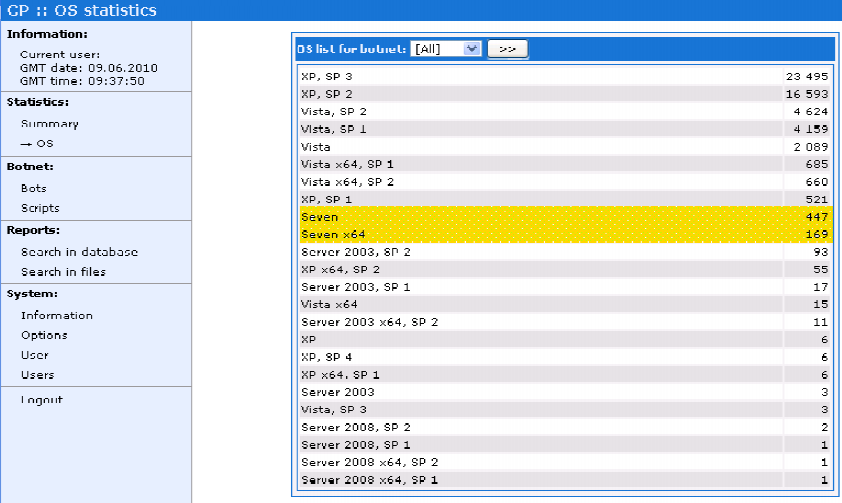
- Windows XP Service Pack 3 users top the chart, followed by Service Pack 2 users
- 33 percent of the infected users are based in the U.S, followed by 17 percent based in Germany, and 7 percent in Spain
- Over 60GB of stolen data from 55,000+ infected hosts found on a fast-fluxed infrastructure
Just like the Kneber botnet, the Mumba botnet is a great example of currently ongoing experimenting on behalf of botnet masters in terms of partitioning their botnets in order to improve operational security, and put contingency planning in place.
Having already anticipated the industry's improving capabilities of reverse engineering their command and control infrastructures, the bad guys are not just diversifying their C&C channels through the use of legitimate infrastructure, but also, starting to realize that massive botnets are sitting ducks waiting to be reverse engineered to the point of shutting them down. Hence, the response with campaign-specific mini botnets using the DIY ZeuS crimeware kit.
Related posts:
- Report: ZeuS crimeware kit, malicious PDFs drive growth of cybercrime
- Modern banker malware undermines two-factor authentication
- The Avalanche Botnet and the TROYAK-AS Connection
This targeted approach allows them to collectively control botnet infrastructures which initially appear to be control by multiple gangs and botnet operators, all hiding under the umbrella of the ZeuS brand, or the brand of a particular web malware exploitation kit.
For the time being, the DIY ZeuS crimeware kit, remains a key driving force for the growth of the cybercrime ecosystem, with the kit's success largely contributed to the use of outdated security flaws on a mass scale. If you want to learn more crimeware, how it works, how it matured from a DIY tool to a key growth factor in the Cybercrime-as-a-Service model, consider going through the The current state of the crimeware threat Q&A.