RSA: Banking trojan uses social network as command and control server
RSA's FraudAction Research Lab is reporting that a crimeware targeting Brazilian banks, is using a popular social network as a command and control server.
According to the company, which acted promptly and took down the profile in question, cybercriminals continue to actively experiment with alternative C&C (command and control channels) using legitimate infrastructure.
More details:
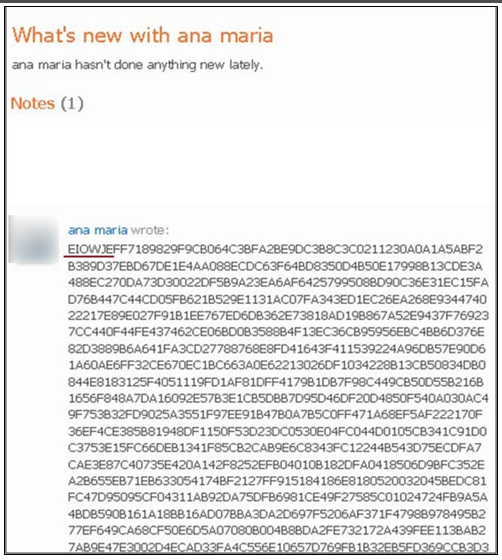
- The cybercriminal behind the crimeware set up a bogus profile under the name of “Ana Maria”, and entered the crimeware’s encrypted configuration settings as text uploaded to the profile.
- After infecting a user’s machine, and installing itself on it, the malware searched the profile for the string EIOWJE (underlined in the above screenshot). The string signified the starting point of the malware’s configuration instructions.
- All the encrypted commands following the EIOWJE string were decrypted by the malware and executed on the infected computer.
This isn't the first time that cybercriminals experiment with managed cloud platforms, or abuse of social networks for command and control purposes, and definitely not the last. Here are some example of known cases where legitimate infrastructure/social networks were used as C&Cs:
- Zeus crimeware using Amazon's EC2 as command and control server
- Twitter-based Botnet Command Channel
- Google Groups Trojan
- Trojan.Whitewell: What’s your (bot) Facebook Status Today?
- The DIY Twitter Botnet Creator
The same mentality was also applied in the “Shadows in the Cloud” cyber espionage campaign, where the malicious attackers once again relied on legitimate infrastructure for command and control purposes:
The attackers also used Yahoo! Mail accounts as a command and control component in order to send new malicious binaries to compromised computers. In total, we found three Twitter accounts, five Yahoo! Mail accounts, twelve Google Groups, eight Blogspot blogs, nine Baidu blogs, one Google Sites and sixteen blogs on blog.com that we being used as part of the attacker’s infrastructure.
Are social networks a heaven for cybercriminals and their botnets? Basically, they are. Social networks offer two of the most important things, a cybercriminal is seeking - potential for scalability where even the shortest time frame for a particular campaign would result in hundreds of thousands of clicks, and the trust factor established by social networks.
Throughout the last couple of years, they started realizing that it's not just the clean network reputation that matters in a social networking environment, but the trusted reputation of the user at any particular social network. For instance, one of the most successful social networking malware, the Koobface botnet which gets the majority of its traffic from Facebook, doesn't rely on bogus user accounts to propagate. Instead, it hijacks the trusted reputation of everyone's friends on a large scale.
RSA's assessment concludes that malware using social networks is currently "the exception rather than the rule". What do you think? Is this the case, or are cybercriminals thinking "the best is yet to come" in the long term? What if today's fake account of Ana Maria, becomes tomorrow's legitimate account of Ana Maria, issuing commands to crimeware-infected hosts in a seemingly innocent fashion from a linguistic perspective?
Talkback.