Seven myths about zero day vulnerabilities debunked
Another month, another zero day flaw has been reported, with malicious attackers logically taking advantage of the window of opportunity, by launching malware serving attacks using it. With vendor X putting millions of users in a "stay tuned mode" for weeks, sometimes even longer, the myths and speculations surrounding the actual applicability of zero day flaws within the cybercrime ecosystem, continue increasing.
Are zero day flaws what the bad guys are always looking for? Just how prevalent are zero day flaws within their business model? Are zero day flaws crucial for the success of targeted attacks attacks?
Let's debunk seven myths about zero day flaws, using publicly obtainable data, an inside view of the cybercrime ecosystem, and, of course, common sense like the one malicious attackers seem to possess these days.
- Zero day flaws are the primary growth factor of the cybercrime ecosystem - Not even close. In 2010, the cybercrime ecosystem is largely driven by the millions of end uses and companies using the Internet with outdated third party applications, and plugins. With the current trends shifting from the exploitation of OS-specific flaws, to the exploitation of client-side vulnerabilities, or good old fashioned social engineering attacks, the rather myopic perspective of the end user/company towards the current threatscape, results in the success of malicious attackers in general. Then, if it's not zero day flaws that the bad guys rely on, what is it that drives their business model? The lack of security awareness internationally, resulting in good click-through rates given they systematically rotate the social engineering themes, the high number of insecure applications/plugins running on an average Internet-connected PC, as well as the current DIY or Cybercrime-as-a-Service state of the ecosystem, allowing unsophisticated attackers to have access to sophisticated attack tools, all contribute to growth of the ecosystem.
- Zero day vulnerabilities is what the cybercriminals are looking for all the time - If they truly were, the cybercrime ecosystem would have never matured into the efficient money machine it has become today. How come? Basically, what the bad guys suddenly realized is that, not only is there a high probability that given enough traffic is hijacked, a huge number of users would be exploitable, but also, that the time and resources they would have spend finding zero day flaws, could be invested somewhere else. This marginal thinking to some, or Keep It Simple Stupid (KISS principle) to others, is what is currently driving their business model - acting based on the harsh reality, instead of conceptualizing on how a perfect(ly) (patched) world is supposed to look like. The myth that zero day vulnerabilities is what the bad guys are after all the time, comes from the concept of the black market for zero day vulnerabilities, a market which has greatly evolved from what it was a few years ago. From OS-specific, to client-side specific, today's pragmatic nature of this market is orbiting around the exploitation of web applications. The only reason why the bad guys have shifted their interests is thanks to the realizations made in point one, namely, now that they are aware that millions of users are susceptible to outdated flaws, targeting popular web applications which would allow them to launch mass SQL injection/or application-specific attacks, consequently hijack the traffic, is what they're currently interested in.
- Zero day flaws are crucial for the success of targeted attacks/advanced persistent threat campaigns - Although zero day flaws appear to be cornerstone for a successful intrusion inside a high profile network, which is presumably better secured than the PC of the average Internet use, numerous cases show otherwise. Perhaps one of the most recent and widely discussed such case, is the Google-China espionage saga. Think malicious attackers, in order to anticipate malicious attackers. Why didn't they try discovering a vulnerability in Google's own browser, Chrome, which should have been the company's logical browser choice in the first place. Intelligence gathering on the fact that there's an IE6 running on a PC, for sure. However, what I'm trying to imply is that there's a high probability that the very same PC which was running Internet Explorer 6, could have also been exploited using ubiquitous flaws found in Adobe's products. How come? It's the insecure mentality, lack of enforced security auditing which would have prevented IE6 running on one of Google's hosts in the first place. As far as targeted attacks/advanced persistent threat type of campaigns are concerned, on a quarterly basis a malicious gang that's clearly interested in infecting high-value targets, redistributes a ZeuS crimeware serving campaign, using exclusively .gov and .mil themed subjects. What's so special about these campaigns in the context of zero day flaws, is that they rely on the manual interaction of the targeted user with the binary hosted on a compromised site, and not on zero day flaws. Although zero day flaws are "desirable", from my perspective they're not crucial for the success of targeted attacks.
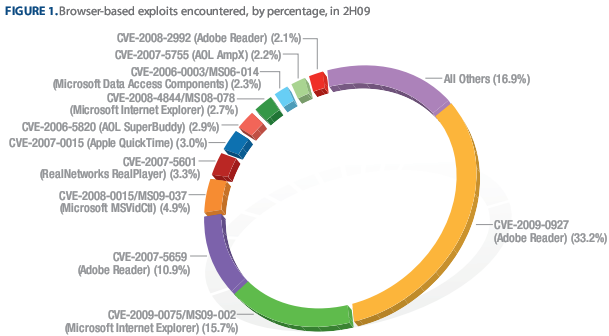
- Operating system specific flaws are more widely exploited than 3rd party application/plugin flaws - Exactly the other way around. According to the SANS Institute's 2009 Top Cyber Security Risks report, application patching is much slower than operation system patching, although client-side vulnerabilities dominate the cyber threat landscape. Microsoft's own Security Intelligence Report Volume 8, also points out that based on their data, third party flaws are more widely exploited than Windows OS specific flaws. Similar conclusions can be drawn by looking at BLADE Defender's Labs real-time infection data, in particular the application targeted, and not the browser targeted. Moreover, the susceptibility of exploitation is one thing, the actual infection rate is entirely another. Case in point, Secunia's recently released report indicates that Apple had the most vulnerabilities throughout 2005-2010. And even if we exclude the obvious differences between Mac OS X's market share compared to market share of Microsoft Windows, theoretically Apple's users are supposed to under constant fire from all angles. Why aren't we seeing this trend? Pretty simple, what the vendor/application centered, to “target them all” exploitation tactic executed by the bad guys has shown us, is the harsh reality, namely the success of their infection rates are not based on the vendor/product with the most flaws, but on the lack of patching on behalf of the end users. Basically, even if the users of a vendor with a relatively modest vulnerabilities count aren't patching, or the vendor doesn't have a well developed communication channel, these users will pop-up as successful infections. Hence, the difference between being vulnerable as vendor, and getting actively exploited thanks to your unpatched users, next to the flawed communication model with them.
- Once a patch for a particular flaw is available, case's closed - One of the most common myths about zero day flaws, is that, once the patch has been released, it's end of story for the vendor as it has now responsibly taken care of the vulnerability. The lack of prioritization of the second stage in the process, namely, communication next to the WGA-wall, results in the current situation, where one of the world's largest botnets, Conficker, continues adding new hosts, despite the fact that a patch has been released. The same situation can be seen with multiple vendors, whose users doesn't have a clue that they're getting themselves infected through flaws which have been patched half an year ago. This lack of second stage communication, can be best seen in Mozilla Foundation's admirable efforts to protect the end user from himself, with such initiatives such as the Plugin Check which also offers plugin checks for users of competing browsers. If only was the same socially-oriented mentality applied by high-trafficked web sites, which compared to anyone else, are in a perfect position to make an impact on a large scale, from a security awareness perspective.
- Full disclosure, in order to motivate a vendor to patch the flaw benefits the community and its users - Although practice has shown that this approach acts as an incentive for vendors to start prioritizing the existence of a flaw, which they have previously denied, the flawed communication model between the vendor and its users discussed in point five, undermines this myth. How come? Pretty simple. The end user who's been using the Internet with outdated 3rd party applications and browser plugins for half an year, will continue doing so, even through they will perceive themselves as "Patch Tuesday" aware. They will also continue being victim of the over-expectations put in the effectiveness of antivirus solutions, forgetting that prevention is better than the cure. This lack of DIY "software asset management" beyond the operation system, or security awareness on the existence of the most widely abused infection tactic by the bad guys, helps them efficiency infect tens of thousands of new users on a daily basis.
- Zero day flaws play a crucial role in the exponential growth of data breaches - According to Verizon's most recent Data Breach Investigations Report, things are in fact even more interesting than that. The report states that based on their data sample, "there wasn't a single confirmed intrusion that exploited a patchable vulnerability". So how are the bad guys compromising these networks/servers, resulting in the exposure of hundreds of thousands of sensitive records? By keeping it simple, targeting the insecurely configured web applications, using customized malware, or basically doing everything else, but emphasizing on the discovery and use of zero day vulnerabilities to achieve their goals.
Did I forget to mention a particular myth? Do you agree, or disagree with some of the points made, and what's your perspective on the myth/speculation in question?
TalkBack.
Image courtesy of Microsoft's Security Intelligence Report Volume 8 report.