Stuxnet 2.0? Researchers find new 'cyber-surveillance' malware threat

[ UPDATE: McAfee says DuQu's main objective is espionage and targeted attacks against sites such as Certificate Authorities (CAs). ]
Researchers at Symantec have sounded an alarm for a new piece of malware with "striking similarities" to Stuxnet, the mysterious computer worm that targeted nuclear facilities in Iran.
The new malware, identified as Duqu, is a highly specialized Trojan capable of gathering intelligence data and assets from entities, such as industrial control system manufacturers, in order to more easily conduct a future attack against another third party.
[ Inside Stuxnet: Researcher drops new clues about origin of worm ]
"The attackers are looking for information such as design documents that could help them mount a future attack on an industrial control facility," according to Symantec's security response team.Symantec said it got a copy of the in-the-wild malware from an unnamed research lab with strong international connections.
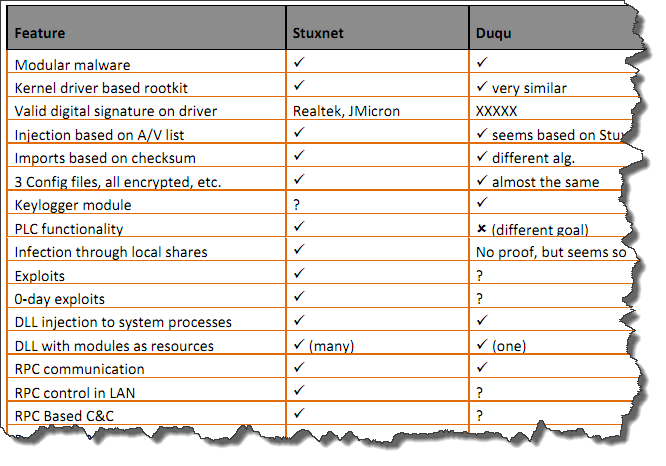
The company found that parts of Duqu are "nearly identical to Stuxnet" but noted that the malware has a completely different goal.
Duqu is essentially the precursor to a future Stuxnet-like attack. The threat was written by the same authors (or those that have access to the Stuxnet source code) and appears to have been created after the last recovered Stuxnet file. Duqu's purpose is to gather intelligence data and assets from entities, such as industrial control system manufacturers, in order to more easily conduct a future attack against another third party. The attackers are looking for information such as design documents that could help them mount a future attack on an industrial control facility.
The company said Stuxnet and Duqu shared the same modular structure, injection mechanisms, and a driver that is digitally signed with a compromised key.
[ Stuxnet: A possible attack scenario ]
Unlike Stuxnet, Symanted said the new malware does not contain any code related to industrial control systems. It was built to be a remote access Trojan (RAT) that does not self-replicate."The threat was highly targeted toward a limited number of organizations for their specific assets. However, it’s possible that other attacks are being conducted against other organizations in a similar manner with currently undetected variants," the company warned.
The attackers used Duqu to install another infostealer that could record keystrokes and gain other system information. The attackers were searching for assets that could be used in a future attack. In one case, the attackers did not appear to successfully exfiltrate any sensitive data, but details are not available in all cases. Two variants were recovered and, in reviewing our archive of submissions, the first recording of one of the binaries was on September 1, 2011. However, based on file compile times, attacks using these variants may have been conducted as early as December 2010.
One of the variant’s driver files was signed with a valid digital certificate expiring August 2, 2012. The digital certificate belongs to C-Media Electronics Incorporation, company with headquarter in Taipai, Taiwan. The certificate was revoked on October 14, 2011.
Symanted noted that Duqu uses HTTP and HTTPS to communicate to a command and control server which is currently operational.
Through the command and control server the attackers were able to download additional executables, including an infostealer that can perform actions such as enumerating the network, recording keystrokes, and gathering system information. The information is logged to a lightly encrypted and compressed local file, which then must be exfiltrated out.
The threat uses a custom command and control protocol, primarily downloading or uploading what appear to be JPG files. However, in addition to transferring dummy JPG files, additional data for exfiltration is encrypted and sent, and likewise received.
Finally, the threat is configured to run for 36 days. After 36 days, the threat will automatically remove itself from the system.
Symantec's researchers believe that the creators of Duqu had access to the source code of Stuxnet.
A technical paper describing the similarities between Stuxnet and Duqu can be found here [PDF].