Super Bowl stadium site hacked, seeded with exploits

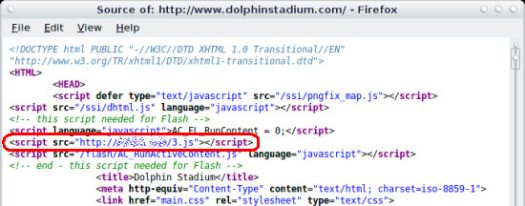
In the attack, which was discovered by malware hunters at Websense Security Labs, the server hosting the site was breached and a link to a malicious JavaScript file was inserted into the header of the front page of the site. Visitors to the site execute the script, which attempts to exploit the vulnerabilities.
According to Dan Hubbard, senior director, security and technology research at Websense, the malicious site hosting the script has been taken offline by law enforcement officials but the hacked Dolphin Stadium site -- which is attracting a lot of Super Bowl-related traffic -- is still hosting the malicious JavaScript.
A visitor to the site with an unpatched Windows machine will connect to a remote server registered to a nameserver in China and download a Trojan keylogger/backdoor that gives the attacker "full access to the compromised computer," Hubbard said.
Sources tracking the threat say the the hosted malware's server host's IP address address keeps changing. This means that unless the owner of the hacked site removes the malicious .js code and secure their server, exploits could start hitting unpatched visitors again.
The attackers are exploiting flaws patched in Microsoft's MS06-014 and MS07-004 bulletins.
[Updated: February 2, 2007 @ 2:42 pm] The dolphinstadium.com Web site has been cleaned but new information suggests another variation of the domain, which redirects to the main site, has now been compromised and actively serving the exploits. "We're not out of the woods yet. This is real-time and on-going," a source said.
Websense has posted an advisory with screenshots.
The most important thing right now is to make sure your Windows machine is fully patched. Users can download and install the updates from Microsoft Update or the built-in Automatic Updates mechanism.
[Updated #2: February 2, 2007 @ 5:13 pm] All the affected Miami Dolphins sites (see Alexa traffic data) have now been disinfected but there is evidence that hundreds of other sites have been hijacked and rigged with the malicious JavaScript code. I've confirmed that the one-line code has been planted on an internal page of the U.S. government's Centers for Disease Control and Prevention Health Marketing site.