US government pays $250,000 for iOS exploit

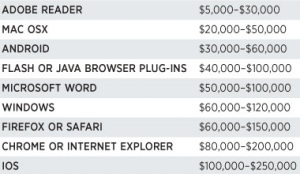
Hackers today are selling zero-day exploits to government agencies via middlemen who charge a commission for setting up the deal. The organizations don't tell the public about the code they pay for because they use it to gain access to their target's devices. Selling to them is considered safer than striking deals with the mafia or other shady organisations because in those cases talks can go south at any time.
Forbes has put together the chart above listing the prices for a single hacking technique, after speaking with multiple sources. According to one middleman, security vulnerabilities in Apple's mobile operating system are very rare thanks to its stronger security, compared to something like Android. While iOS exploits are the most lucrative, they're not, however, the only ones that can bring a six figure pay day.
Browser vulnerabilities in Chrome, Internet Explorer, Firefox, and Safari are next, with the more popular browsers getting hackers more cash. These are followed by the most popular Microsoft software (Windows and Word). Last but not least, if you can't find a security hole in a browser, there's always Flash and Java that you can go after to get yourself up to $100,000.
The price goes up if the hack is exclusive, works on the latest version of the software, and is unknown to the developer of that particular software. Also, more popular software results in a higher payout. Sometimes, the money is paid in instalments, which keep coming as long as the hack does not get patched by the original software developer.
See also:
- New iPad jailbroken on day one
- Teenager hacks Google Chrome with three 0day vulnerabilities
- Pwn2Own 2012: Google Chrome browser sandbox first to fall
- CanSecWest Pwnium: Google Chrome hacked with sandbox bypass
- Researchers hack into newest Firefox with zero-day flaw
- Pwn2Own 2012: IE 9 hacked with two 0day vulnerabilities