Which are the most commonly observed Web exploits in the wild?
M86Security's newly released report "Security Labs Report - July – December 2011 Recap", details some of the most commonly observed Web exploits currently in the wild, as well as offers a detailed overview of the most popular web malware exploitation kits.
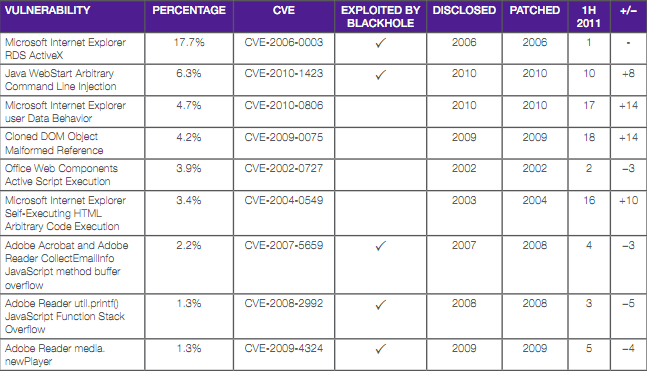
Some of the most commonly observed exploits are:
- Microsoft Internet ExplorerRDS ActiveX - 17.7%
- Java WebStart Arbitrary Command Line Injection - 6.3%
- Microsoft Internet Explorer user Data Behavior - 4.7%
- Cloned DOM Object Malformed Reference - 4.2%
- Office Web Components Active Script Execution - 3.9%
- Microsoft Internet Explorer Self-Executing HTML Arbitrary Code Execution - 3.4%
- Adobe Acrobat and AdobeReader CollectEmailInfo JavaScript method buffer overflow - 2.2%
- Adobe Reader util.printf()JavaScript Function StackOverflow - 1.3%
- Adobe Reader media.newPlayer - 1.3%
- Microsoft Internet ExplorerTable Style Invalid Attributes - 1.1%
- Adobe Reader GetIconJavaScript method buffer overflow - 1.1%
- Java Plugin Web Start Parameter - 1.0%
- Windows Help and SupportCenter Protocol Handler - 0.9%
- Microsoft Internet ExplorerDeleted Object EventHandling - 0.8%
- IE STYLE Object InvalidPointer ReferenceVulnerability - 0.6%
More from M86Security's report:
Exploits in the second half of 2011 targeted a variety of products, including Microsoft Internet Explorer, Oracle Java, Microsoft Office productsand quite commonly, Adobe Reader and Adobe Flash. Security fixes for some of these vulnerabilities have been available for years, whichpoints out a continuous problem: Many users and organizations do not patch all their installed software in a timely manner, and attackersleverage this weakness to their advantage.As the table shows, more than half of the most exploited vulnerabilities are used by the prevalent Blackhole exploit kit.
Based on the report, the BlackHole web malware exploitation kit remains the most popular client-side exploits serving kit, representing 95.1% of observed malicious URLs. M86Security contributes the growth of the BlackHole web malware exploitation kit due to the frequent updated issues by the coders of the kit, including the very latest remotely exploitable vulnerabilities.
The report's findings confirm the findings from previously released reports indicating that outdated and already patched vulnerabilities remain among the key driving forces for the success of cybercrime.
End users are advised to ensure that they're running the latest versions of popular software, as well as browser plugins, to avoid exploitation through client-side exploits.