XSS worm at Justin.tv infects 2,525 profiles
A XSS worm was crawling across Justin.tv, the popular lifecasting platform at the end of June, details of the incident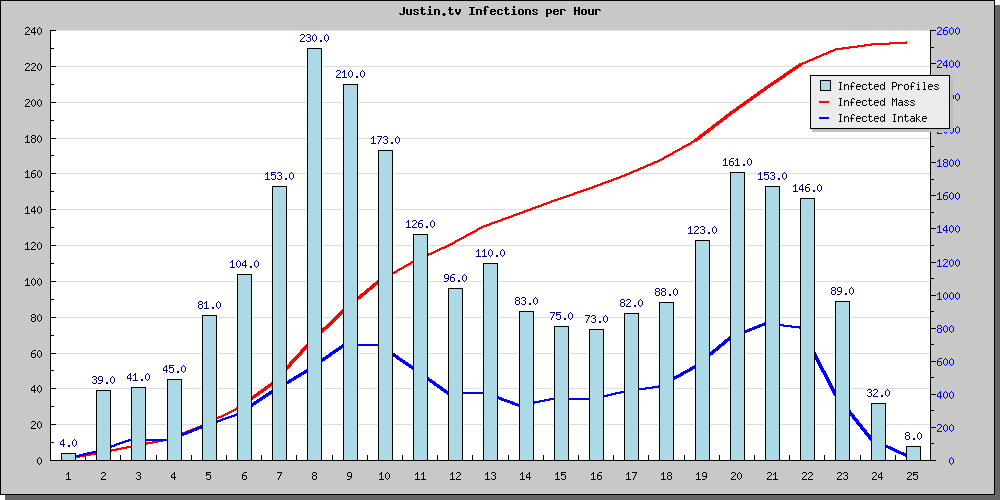
"As of 'Sat, 28 Jun 2008 21:52:33 GMT' - An XSS worm was released on this website, this was and is meant only for research purposes. It was successfully executed and lasted roughly around 24 hours.
We have recorded such records making it possible for us to create graphical images graphing the progress of this XSS worm as it infected each profile upon the last being viewed. The XSS Vulnerability was discovered and fixed during 'Sun, 29 Jun 2008 21:12:21 GMT', with an after mass of 2525 profiles.
This actually is the very first XSS worm which we have unleashed, and it was solely upon research reasons; non-malicious at all :)
We've contacted the JTV Programmers prior to the fixing of the XSS worm and have sorted things out with them and made sure that they knew NO information such as IP Address, Cookies, Sessions and further information which poses private is not to be released. After that I put myself forward and found another XSS in turn to prove that I was dedicated to helping JTV out in any further possible vulnerabilities", says x2Fusion. "
Justin.tv fixed it shortly after users started complaining :
"On Saturday we started to receive emails from users saying that their account had been compromised. On Saturday night we found a vulnerability that allowed someone to gain access to another users account without needing their username and password. Emmett worked tirelessly to fix the bug and released a patch on sunday morning. We were informed that as a result of the first vulnerability, personal communications from a number of justin.tv users were posted on flickr for all to see. We greatly regret that this occurred and apologize that we were not able to find and fix this vulnerability sooner. On tuesday and similar vulnerability was found and it was fixed within 2 hours."
The majority of social networking sites have all be subject to the efficient exploitation of a single XSS flaw, leading hundreds of thousands, sometimes millions of users affected by XSS worms. Orkut, MySpace (as well as a second possibility for a QuickTime XSS flaw), GaiaOnline, Hi5 are just the tip of the iceberg, since a great deal of currently unfixed vulnerabilities can easily become XSS worms if that's what someone wants to achieve.
Adding a second layer of protecting for the end users, with the first one being the site's own responsibility for self-auditing themselves, widely used Internet browsers are finally contributing to the second layer of protection, with Mozilla's Site Security Policy and IE8's Cross Site Scripting Filter, aiming to protect the user even if the site itself remains vulnerable. Let's see how long before malicious parties start bypassing the built-in protection mechanisms, and publicly demonstrate this on a large scale.