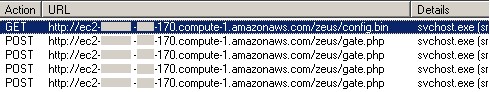
Zeus crimeware using Amazon's EC2 as command and control server
UPDATED: ScanSafe posted an update stating that "In the past three years, ScanSafe has recorded 80 unique malware incidents involving amazonaws, 45 of which were in 2009, 13 in 2008, and 22 in 2007."
Security researchers have intercepted a new variant of the Zeus crimeware, which is using Amazon's EC2 services for command and control purposes of the botnet. The cybercriminals appear to be using Amazon's RDS managed database hosting service as a backend alternative in case they loose access to the original domain, which would result in the complete loss of access to the compromised financial data obtained from the infected hosts.
Would 2010 be the year when crimeware will dive deep into the cloud, in an attempt to undermine the security industry's take down operations? With the clear migration towards the abuse of legitimate infrastructure we've observed throughout the entire 2009, this may well be the case.
Despite the fact that this is the first publicly reported case of Zeus crimeware (Modern banker malware undermines two-factor authentication) campaign abusing Amazon's cloud-based services, popular Web 2.0 services have also been under fire in recent months.
From the use of Twitter, to Google Groups and Facebook as command and control servers, these experiments clearly indicate that cybercriminals are cloud-aware, which isn't surprising given that from a distributed computing perspective, some of biggest botnets currently online can easily top the Top 500 Supercomputing list.
It's traffic camouflaging in the sense of making it harder to blacklist and detect potentially malicious activity hidden within the traffic stream between the infected host and a legitimate service.