Mac fail: SSD security

SSDs, Mac OS X and data security don't mix. Not only does the standard file delete not delete files - which savvy readers already know, but even the Mac's "Secure Erase Trash" function leaves 2/3rds of a file recoverable.
"Fake Erase" perhaps?
The SSD problem Vendors have struggled to make flash SSDs look like disk drives even though the underlying media are very different. Hard drives associate a physical location with each logical block address (LBA). SSDs don't.
And that's the security problem.
Our secure file deletion tools assume that the data is stored in a set physical location. If the LBA is written to, the existing data at that LBA can be presumed to have been overwritten. (Bad block replacement is the big exception to that general rule.)
But on flash-based SSDs, the firmware that makes flash look like a disk - the flash translation layer (FTL) - is constantly changing the physical address of the data. When the OS issues an overwrite, the FTL overwrites only the most recent location the data - leaving older locations untouched.
The research This is a problem for all file systems, but according to a paper presented at FAST '11 last week, Mac OS 10.6 Secure Erase Trash command did an especially poor job.
The UC San Diego researchers, Michael Wei, Laura M. Grupp, Frederick E. Spada and Steven Swanson, ran 14 different file overwriting utilities 3 times on SSD and USB drives. They then disassembled the drives to electronically access the flash chips to see what data they could recover.
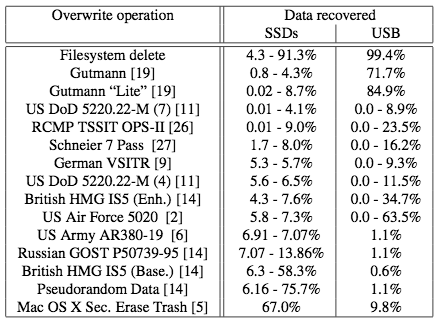
Here's the table of their results:
Oddly enough, Secure Erase Trash was much more effective on cheap USB drives than on SSDs - the reverse of most of the other overwriting techniques.
What about Windows? Windows does not offer a command equivalent to "Secure Empty Trash" so they aren't misleading users about their data security. Apple chooses to offer "Secure Empty Trash" in the Finder menu so they need to ensure it does what they say.
The Storage Bits take Apple consumes 50% of the world's NAND flash - and their flagship OS can't securely delete SSD data. Isn't total control of the hardware and software supposed to improve integration?
Who, exactly, is minding the store?
No doubt the Mac OS X file system team can hack the already much-hacked HFS+ to fix this problem. But how is it that no one on the engineering team caught this problem?
Surely some engineer - from Toshiba or Samsung, flash and flash controller vendors to Apple - or in the OS X group, raised the issue of security. If that didn't flag the problem, why didn't the OS team's regression testing find it?
HFS+ is long past due for retirement. It is time for Apple to get serious about how it's products handle customer data. As an SSD-based Mac owner I'm more than a little peeved at the company's cavalier attitude.
Note that Apple's other major OS - iOS - wasn't tested. But who can have a warm feeling about the iOS remote delete facility now?
Comments welcome, of course. I'll have more on the UCSD paper later this week, but if you can't wait here's a link to the pdf of Reliably Erasing Data From Flash-Based Solid State Drives. Update: I added the What about Windows? paragraph above in response to the 1st comment.