For the love of God, please secure your wireless networks

"Ring Ring."
It's early Sunday afternoon, my wife picks up the phone. A few minutes later, she walks into my office. From the tone of her voice, I can tell that she's been speaking to my Mother-in-Law, Sandy, and that something technical in nature, up in the place I used to call home, back in good ol' Northern New Jersey has gone awry.
Sandy's experiences with her PC have been fodder for a lot of interesting articles over the years. Interesting not because what Sandy encounters is particulary unusual, but because what she encounters are the kinds of obstacles that us technical, PC-savvy types see as simply minor annoyances but end up being total showstoppers for a novice end-user.
"She needs to talk to you. Her printer isn't working."
I looked back at my wife, while cupping a freshly-pulled espresso lungo. "She should call Epson tech support."
"The Epson people said it was a Windows problem."
I scowled, with my best grumpy-cat face. "Rachel, what the hell, do I look like I work for Microsoft or something?"
"Okay, put her on the phone."
One of the best tools for doing technical support remotely is a free program called TeamViewer. I use it to support my parents, who live locally in Florida, and also for my Mother-in-Law, who lives in New Jersey. It's multi-platform, so it runs on Windows, Mac as well as Linux.
Similar to screen sharing and remote access apps like GotoMeeting, GoToMyPC or WebEx, it's a free program when used strictly for personal, non-commerical use. I have it installed on every machine for every friend or family member I have to occasionaly help out with support issues on.
I remoted into my Mother-In-Law's PC, and noticed she was wirelessly connected to "Linksys". Well, that's odd. So I went into the router config -- which was set to the default "root/admin" combo typical of Linksys SOHO routers, and noticed it was an unsecured network.
"What the heck? I don't remember setting the router this way."
And maybe I was tired, or maybe I simply forgot, but it eluded me for about ten minutes that what I had logged into was a WRT-54G, an older, but extremely popular model of Linksys Wireless-G router. I distinctly remembered buying Sandy a brand new Wireless-N router last year, a Linksys EA-2700.
And then it dawned on me. I wasn't in Sandy's router. I was in... her neighbor's.
Well, there's your problem, mom!
I had re-built Sandy's laptop during the winter break when she was down here visiting with my Father-in-Law, Bob. I purchased her a Windows 8 upgrade license, a new copy of Office, and configured it to use her model of printer.
Now, Sandy's printer, an Epson Workforce 645, can be used wirelessly, over a Ethernet connection, or it can be directly connected via a USB port. For whatever reason, the Epson tech could not get the printer working with Sandy over the phone. I figured out what happened though.
First, the Epson phone tech didn't realize that Sandy was connected to an unsecured wireless network. How she got connected to it doesn't really matter. She could have clicked on the first network that popped up by accident (because it was called "Linksys" which is the same brand as her router) or the Epson tech simply assumed that was the correct network when she told him what brand of router she had.
I was not privvy to the tech support conversation, but Sandy did tell me that the tech instructed her to uninstall/re-install all her printer drivers, and then determined they "Could not get the PC to work with the printer."
An unsecured Linksys WRT-54G is the wireless security equivalent of keeping the front door of your home wide open, year-round.
For whatever reason, the PC and the Epson All-in-One lost the wireless connection to her EA2700 router. Windows 8's default behavior is not to connect to any unknown wireless network unless the user instructs it to, secured or otherwise. This is a security feature. Not "A Windows Problem".
Jersey has been having lightning storms and random power outages a lot in the last year or so, so it wouldn't surprise me if there was some temporary connectivity issue involved in the mix, combined with simple user error that caused this condition. As well as being stuck with a telephone support tech at Epson that obviously doesn't understand the fundamentals of PC and TCP/IP networking.
Either way, an unsecured wireless network tripped Sandy up. And I suspect that this sort of thing is not uncommon.
How did I fix it? Simple. I had Sandy connect an ethernet cable from her router to the printer, and another one from her laptop to her router, since it never leaves her desk, and installed/upgraded the Workforce 645 drivers and firmware.
That Epson's tech couldn't figure this out is laughable, but all sorts of end-user to tech phone communication issues can contribute to an unsatisfactory support experience. I'll give them the benefit of the doubt on this one.
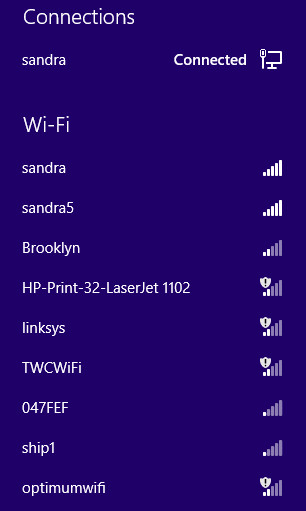
In any case, in the course of fixing this minor printer issue via remote, I discovered that Sandy's neighborhood was absolutely infested with unsecured wireless networks.
The screen shot at the header of the article says it all. We've got the ubiquitous "Linksys" that tripped up Sandy, a Time Warner Cable public access Wi-Fi gateway, an Optimum Online public access Wi-Fi gateway, and a few others that didn't show up in the screen shot, such as a Comcast XFINITY W-Fi gateway, and a large number of unsecured privately-owned routers built by Netgear, D-Link, Apple and other usual suspects.
In the case of the cable companies providing public Wi-Fi access points for their subscribers, I have to say I am a bit annoyed that they tend to use unsecured, SSID broadcast Wi-Fi networks as entry points.
My general understanding is that they require registered MAC addresses in order to gain actual access, but still, it potentially can cause connectivity issues with devices that will attempt to default lock onto them, and it simply pollutes the neighborhood with unnecessary stuff showing up on our respective devices and confuses end-users.
Now, private end-users with unsecured WLANs? These people are really asking for trouble. Sandy's neighborhood is a bedroom community in Northern New Jersey, with nice houses in residental developments bordering a golf course and a country club. This is exactly the type of neighborhood that "wardrivers" stalk, looking for systems for which they can gain entry and steal information.
In the defense of most SOHO networking equipment manufacturers, they have gotten a lot better about creating default settings that require WPA2 encrypted WLANs out of the box. However, there are still many older routers still on the streets, such as the WRT-54G, which aren't secured and are running in default configurations.
An unsecured Linksys WRT-54G is the wireless security equivalent of keeping the front door of your home wide open, year-round.
Sandy's community is primarily composed of folks aged 60 and older. They've been living in their homes for at least a decade or longer, and have had broadband probably for at least that long. I don't want to make any sweeping generalizations about older people, but a lot of folks do not replace SOHO networking equipment until it actually breaks, and many of these older people are not technically savvy. So they are the perfect target for wardriving attacks.
I suspect that most of the people reading this piece are not the types to run unsecured networks. But if you do see them in your neighborhood, try to find out who owns them, and educate whoever is running them to replace their older router equipment (particularly if they are only capable of using WEP, as opposed to the newer WPA2 standard) and to set the appropriate WLAN passwords and to use Wi-Fi Protected Setup (WPS) with their devices when possible.
And while I am generally not of the opinion that governments should interfere with the usage of our own electronic equipment, I do think that anyone who runs an unsecured WLAN should be subject to fines, because they endanger themselves and the people living in their households, as well as those people who they are potentially sharing data with.
Is your neighborhood infested with unsecured wireless networks? Talk Back and Let Me Know.