Google free public DNS services were briefly corrupted

Without the Domain Name System (DNS), we're all lost on the Internet. DNS provides the service that translates our human readable Web addresses such as google.com to their real, but mysterious Internet Protocol version 4 (IPv4) addresses, such as 8.8.8.8 or IPv6's 2001:4860:4860::8888. The problem with this master yellow pages directory to the Internet is that DNS records themselves can be corrupted or your communications with the DNS servers interrupted by a man-in-the-middle (MiM) attack.
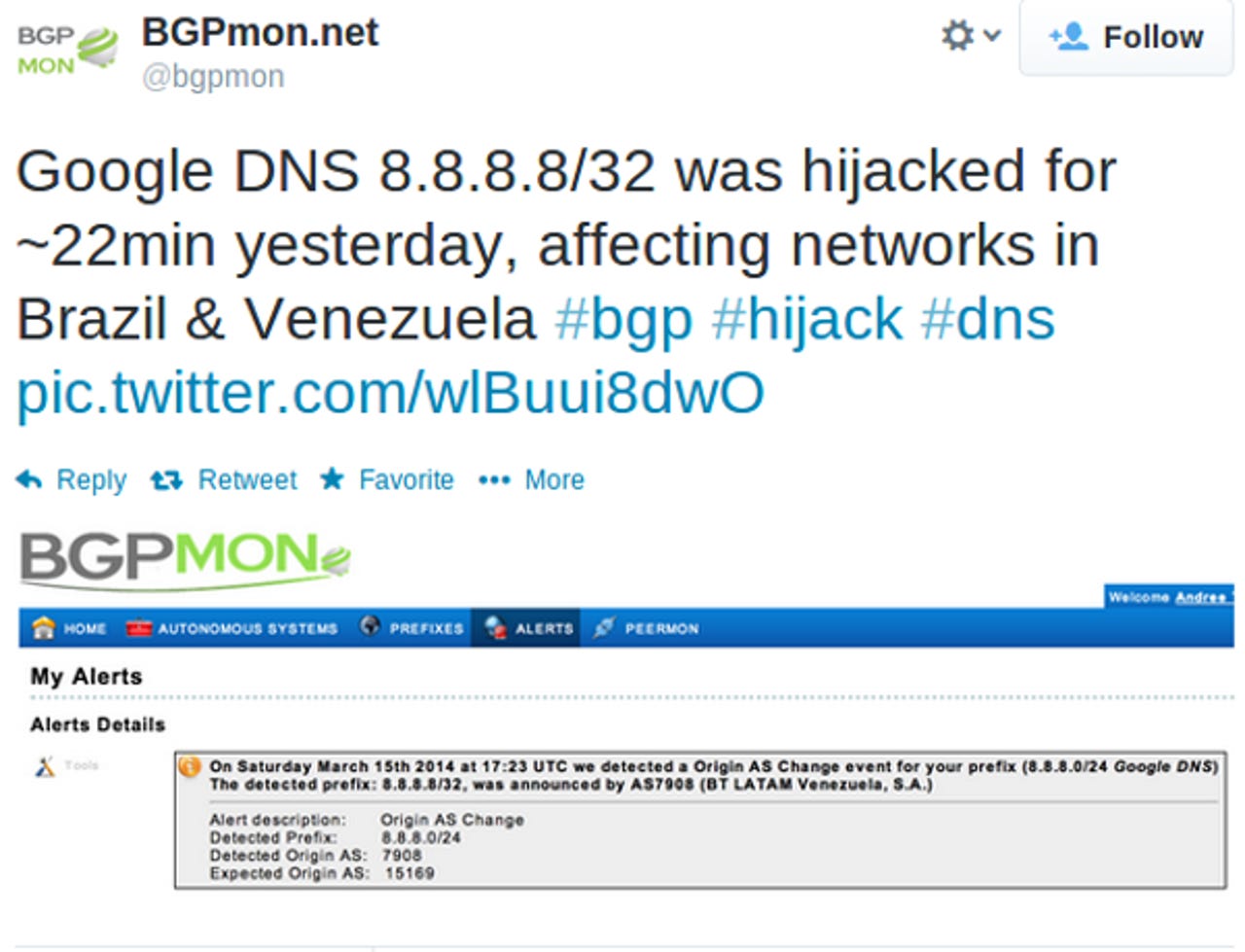
On March 16, the network security company BGPmon reported that Google's Public DNS server, 8.8.8.8, was hijacked for Internet users in Brazil and Venezuela for 22 minutes. During this so-called MiM attack, anyone seeking a Web site, e-mail server, or the like was redirected to a site belonging to British Telecomm's Latin America division. The assault seems to have been result of Border Gateway Protocol (BGP) hijacking.
Google's Public DNS servers are used for "130 billion DNS queries on average (peaking at 150 billion) from more than 70 million unique IP addresses each day." That makes Google the most popular free public DNS service in the world. Public DNS services, such as those offered by Google and OpenDNS, are used by savvy Internet users who want the fastest possible look-up speeds for their Web browsing.
Featured
Google has adopted Domain Name System Security Extensions (DNSSEC) by default for its DNS servers. This prevents the far more common DNS cache poisoning attack.
Many companies, however, still don't use DNSSEC nor have so-called "open" DNS servers. Both make their DNS servers more vulnerable to attacks and enable them to be used in distributed denial of service (DDoS) attacks.
The BGP attack itself may have arisen from the well-known flaw that there's no way to check if a particular IP address belongs to a particular Internet Service Provider's address range. Making use of this vulnerability wasn't easy. It required that an important router at a major South American ISP be under the control of an attacker
In this case, while the attack kept users from using the Internet, it seems to have no malicious designs. Given that the "attack" didn't direct users to a rogue DNS server pointing users to malware-loaded sites, I suspect the real problem was that someone briefly misconfigured a router. This would not be the first, or 101st time this kind of incident happened. Just a typo in a configuration file is enough to send users to a wrong address for their DNS queries.
We don't know exactly what happened. Google was asked for a comment and hasn't responded yet. In this particular case, I suspect Google had nothing to do with it, and my money is on an accident rather than BGPmon's attacker. That said, the incident does underline how fragile the Internet is even now.
Related Stories: