Hacker swarm attacks dummy critical infrastructure honeypot

Fake industrial control systems set up to test threats against internet-connected critical national infrastructure came under repeated attack from hackers.
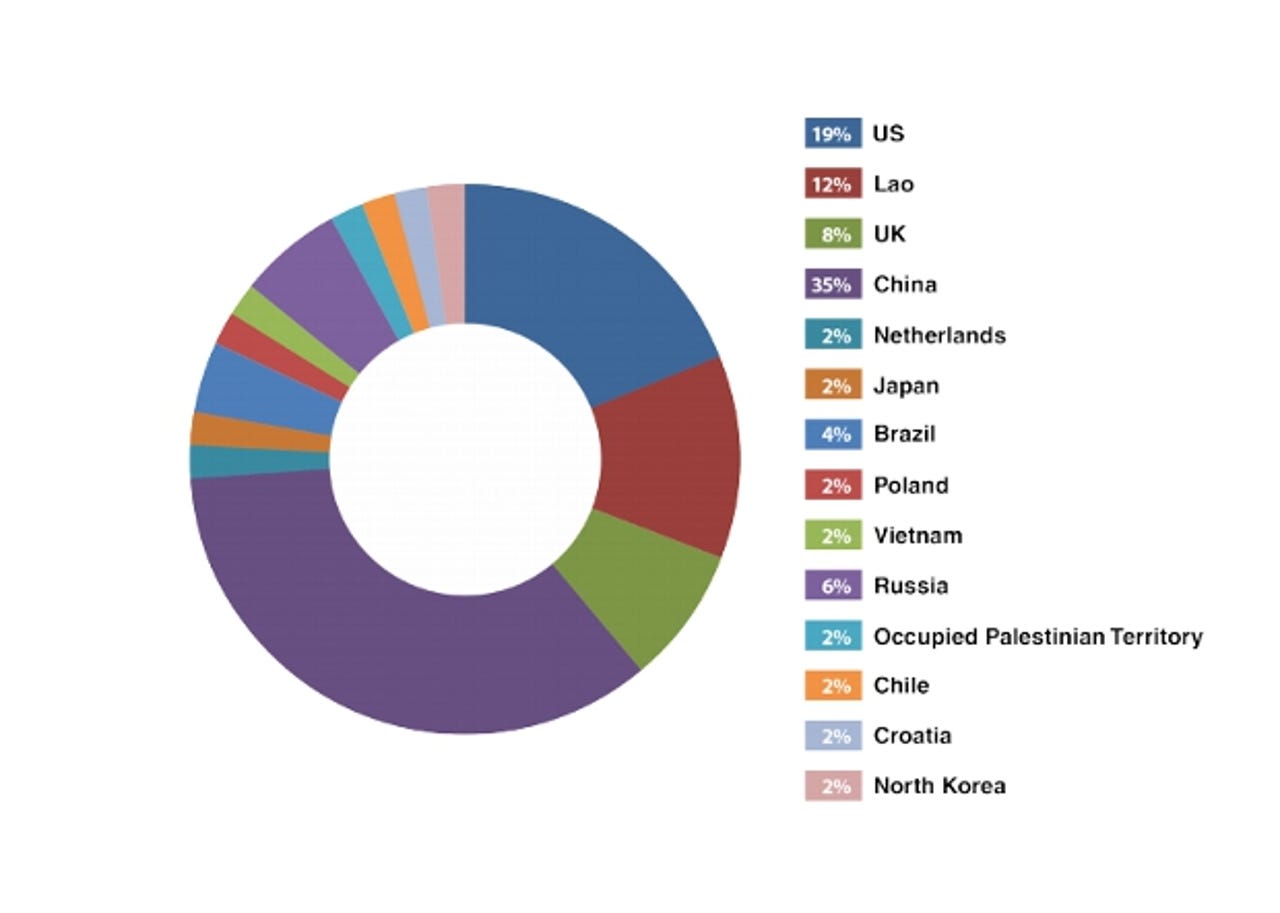
Internet-connected systems that mimicked the ICS/Scada devices used to help run many power and water plants were set up by security firm Trend Micro. Over the course of the 28 days that the honeypot systems were active Trend Micro detected 25 attacks from 11 different countries, according to research presented at the Black Hat 2013 conference in Amsterdam on Friday.
Out of the attacks, 12 were targeted, and 13 were repeated several times by the same actor, indicating they could have been automated.
The actions carried out during the attacks ranged from attempts to change the CPU fan speed on systems purporting to control a water pump to gathering systems information.
These attacks were not automated 'drive-by' attacks targeting any internet-connected system, such as SQL injection, but were rather specific attempts to compromise internet-facing ICS/Scada systems, the researchers said.
"This includes unauthorised access to secure areas of sites, modifications on perceived controllers, or any attack against a protocol specific to ICS/SCADA devices like Modbus," Trend Micro researcher Kyle Wilhoit wrote in the report.
The majority of the attacks stemmed from China and the US.
"In sum, China accounted for the majority of the attack attempts at 35 percent, followed by the US at 19 percent," Wilhoit wrote.
The subject of ICS/SCADA vulnerability became high profile following the exposure of the Duqu and Stuxnet malware that targeted such systems. According to recent research conducted by ICS-CERT, in 2012 alone, 171 unique vulnerabilities affecting 55 different ICS vendors were found.
The fake systems were given a range of vulnerabilities typically found across similar systems. To maximise the exposure the three honeypot systems used three different static internet IP addresses in different subnets in the US.
Researchers simulated three types of ICS/Scada systems. A programmable logic controller (PLC) system running on a virtual instance of Ubuntu hosted on Amazon EC2. This was configured as a web page that mimicked a control station for water pressure station.
A web server that mimicked a human machine interface connected to a PLC production system, hosted on a Dell DL360.
The final machine was an actual PLC device called a 'Nano-10' from Triangle Research. It was set up to mimic temperature controllers in a factory and had temperature, fan speed, and light settings that could be modified.
As part of the research the firm also carried out Google searches to indentify ICS/Scada systems exposed to internet that did not have security mechanisms to prevent unauthorised access.