How did European bank malware steal $47 million?

Just how is 36 million euros ($47 million) stolen through mobile malware?
A paper released by Checkpoint suggests that hackers working in Eastern Europe have systematically been able to swipe approximately $47 million through the use of a trojan that infiltrates smartphones. The infestation, dubbed "Eurograbber", is a trojan variant based on the Zeus and Zitmo banking malware.
According to the firm, by intercepting two-step authentication text messages sent to mobile phone users -- with a particular bend towards BlackBerry and Android models -- amounts ranging between 500 and 250,000 euros have been stolen from over 30,000 banking customers.
Eurograbber hits in multiple stages. After unknowingly clicking on a phishing email -- and possibly through visiting a malicious website -- the trojan is downloaded on to the victim's computer. Once a banking customer logs into their bank account, the banking session is intercepted and malicious javascript code is injected into the banking page. The customer is then notified of a "security upgrade" and instructed to click on an attached link via an SMS message sent to their submitted mobile phone number.
This stage triggers a file download to the customer's mobile with a variant of the Zitmo trojan customised for different operating systems, namely Android, BlackBerry and Windows, and the customer receives a "verification code" which they must input through their desktop on the now-malicious banking page.
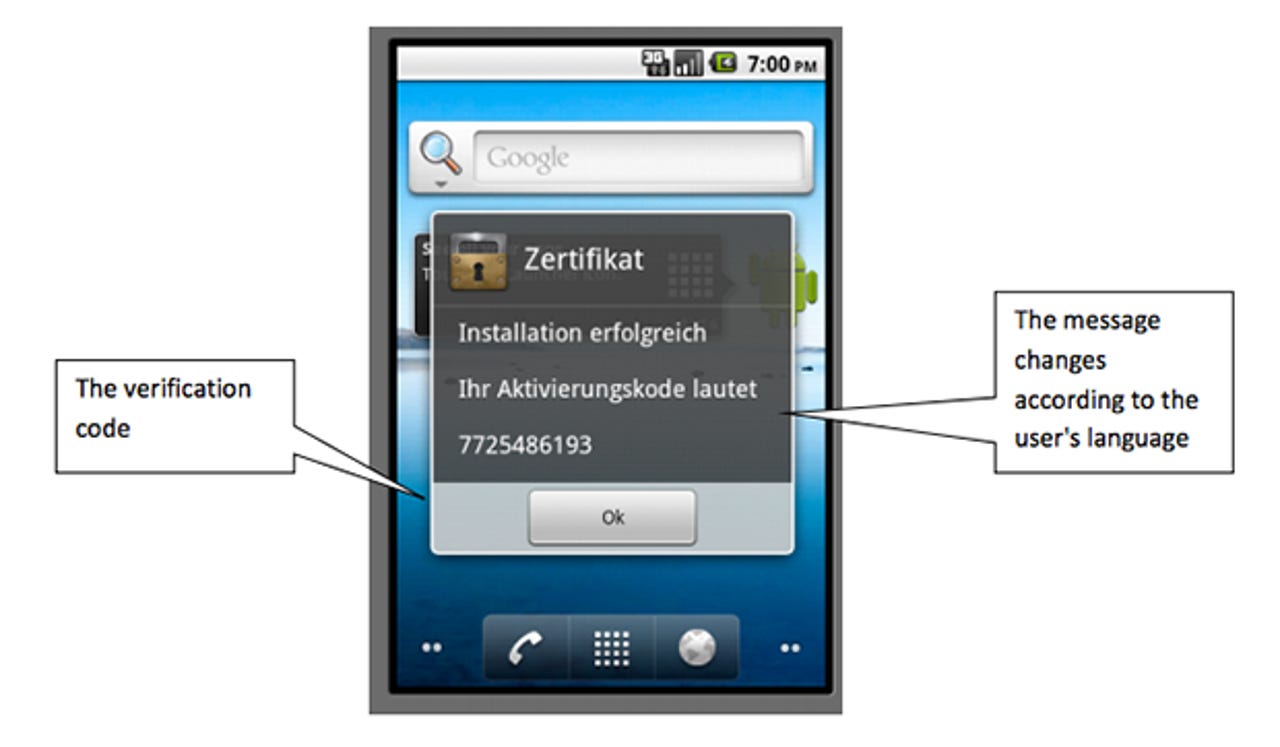
Once input, the javascript informs the banking customer the security upgrade is complete, and the trojan's work can begin.
Banks in Europe often use "transaction authorization numbers" (TAN) to prevent fraudulent online transactions, in the same way that PayPal now offer a service which requires you to input an SMS-sent key before accessing your account online. The Eurograbber trojan's sophisticated attack circumvents this two-factor authentication by monitoring banking activity once installed, and intercepts the SMS to silently transfer money out of a bank account.
Interestingly, Checkpoint says that there is no evidence of these transactions on web statements -- as the trojan also intercepts the confirmation text sent by the bank -- making the trojan a silent background menace that operates until it's too late. To prevent exposure, only a small percentage of the bank balance is transferred at a time.
In order to execute these kinds of attacks, Eurograbber relays banking activity back to a team of attackers, who silently complete any transactions they wish. A Command & Control (C&C) server infrastructure was created through SQL databases which were linked to different domain names, and in addition, a layer of proxy servers were used to keep detection at a minimum.
The Eurograbber trojan, although targeted at Android and BlackBerry smartphones, has also been found to include variants designed for Windows models. According to the research firm, both corporate and private banking users have been affected.
Attacks began in Italy, and soon the exploit hit the shores of Germany, Spain and Holland. Cases have only been documented in Europe so far, but it is possible that countries outside of the European Union may also eventually become targets of the Eurograbber trojan.
Image credit: Checkpoint