iPhones most 'vulnerable' among smartphones

More software vulnerabilities exist in iOS compared to the other operating systems, and a SourceFire executive said this is due to the iPhone's popularity, and Apple's strictly controlled app store which drives cybercriminals to find vulnerabilities in the operating system instead.
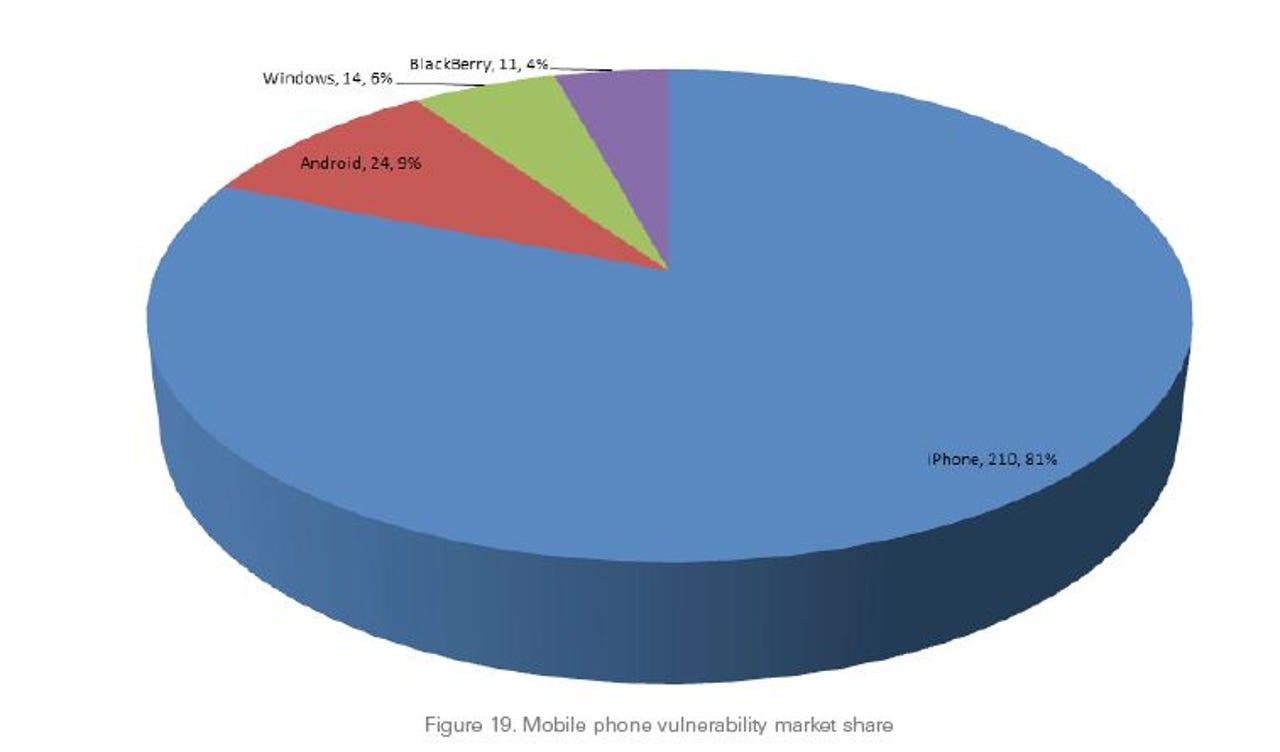
According to SourceFire's "25 Years of Vulnerabilities" study released in early March, which analyzed vulnerabilities from the Common Vulnerabilities and Exposures (CVE) data and National Vulnerability Database (NVD), the majority of mobile phone vulnerabilities have been found in Apple's iPhone. The database provides 25 years of information on vulnerabilities to assess, spanning from 1988.
210 vulnerabilities were found in Apple's smartphone, giving iOS 81 percent of the mobile phone vulnerability market share. This is more than the total number of vulnerabilities in Android-based, Windows-based and BlackBerry-based smartphones combined, at 19 percent.
In an interview with ZDNet Asia, Yves Younan, senior research engineer at SourceFire's Vulnerabilities Research Team and author of the report, pointed out the finding was "surprising". It was also "interesting" as Apple has had significant CVE growth year over year, despite the operating system implementing more security features in subsequent iterations, he added.
Even though Android devices have topped the mobile phone operating system market share, iPhones are still popular among consumers, which is why cybercriminals are driven to find loopholes in the Apple's operating system, Younan explained.
With Android devices, cybercriminals see less reason to look for vulnerabilities to penetrate smartphones, he added. Android's open platform already easily opens up for third party and malicious apps to be easily created for users to download, he explained.
On the other hand, this cannot be done with the iOS store due to Apple's strict control of apps that are published. This is why cybercriminals are driven to find loopholes in the software system of Apple instead, he added.
As for Windows, the low number of vulnerabilities could be due to the fact it is not a popular operating system yet, Younan pointed out, but declined to comment on vulnerabilities in the BlackBerry operating system.
Enterprises must prepare for, tackle vulnerabilities
It was also found in the report the overall number of vulnerabilities with a high severity rating increased significantly until 2007, when it reached a high of 3,159. Since then, it tapered off and fell to 1760, despite more vulnerabilities being discovered in 2012.
What the study shows is vulnerabilities are here to stay, Younan noted.
Moving forward, enterprises must look at how to deal with them, and mitigate having a cyberattacker exploit the vulnerability, by installing mitigation on operating systems or using security products, he said.
"[Enterprises] should also plan for potential compromises including how they will rebuild and ensure the integrity of the data," Younan added.