Large Internet Explorer update headlines June Patch Tuesday

On Tuesday, Microsoft released seven security bulletins and updates addressing a total of 66 vulnerabilities.
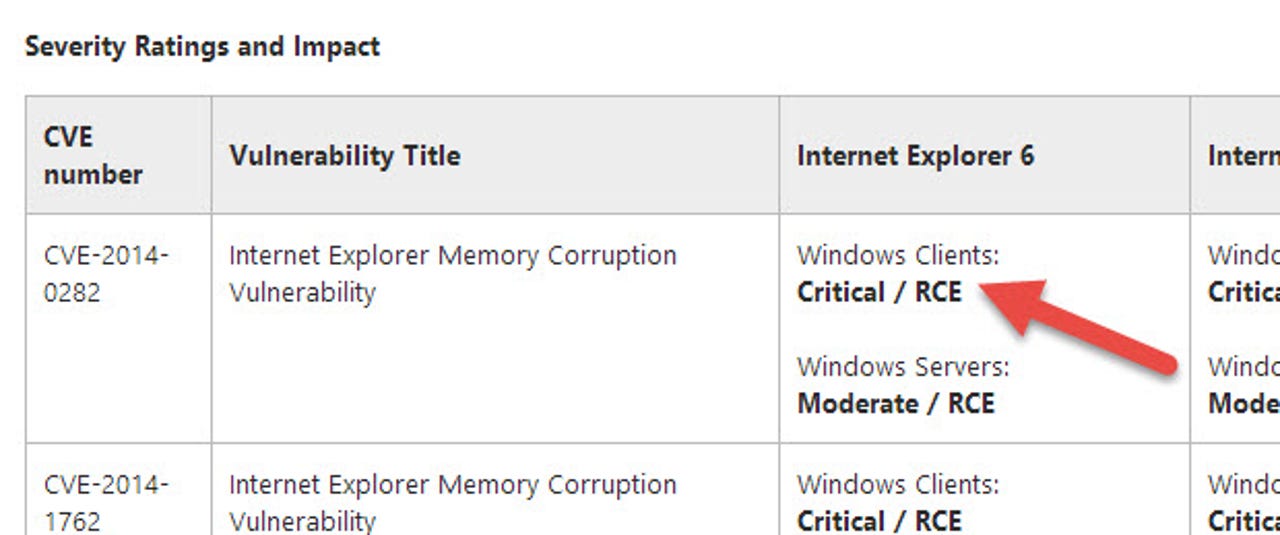
In total, 59 of them are in a single update, a Cumulative Update for Internet Explorer. That update and another affecting Windows and Office are rated critical. One of those IE vulnerabilities had been publicly disclosed.
- MS14-035: Cumulative Security Update for Internet Explorer (2969262) — Nearly all of the 59 vulnerabilities fixes in this update are rated critical on at least one version of Windows and Internet Explorer, but the mix of severities and versions is complex. Microsoft credits at least 32 researchers for disclosing these vulnerabilities (some are anonymous). Microsoft has also been collecting these vulnerabilities for some time; one of them, CVE-2014-1770, was reported to Microsoft over six months ago by HP's Zero-Day Initiative. ZDI waits to disclose until the vendor issues a fix, but their rules state that they will disclose in any case after six months.
Another interesting characteristic of this update is that Microsoft includes information as to whether Windows XP is affected, although they try to be slightly oblique about it:
We can also confirm from our own testing that Windows XP systems hacked to look like Windows POSReady do receive this and other updates.
- MS14-036: Vulnerabilities in Microsoft Graphics Component Could Allow Remote Code Execution (2967487) — This update addresses two vulnerabilities in Windows, Office 2007 and 2010 and Lync, an interesting combination of products. Both vulnerabilities are critical on at least some of the platforms.
The remaining updates are for vulnerabilities with a maximum severity of Important. Each update addresses a single vulnerability.
- MS14-030: Vulnerability in Remote Desktop Could Allow Tampering (2969259) — This is an unusual vulnerability, which could allow an attacker to modify the traffic content of an active RDP session. It is blocked by Network Level Authentication (NLA) and good firewall practices and, in any case, Microsoft considers it unlikely that successful exploit code could be written.
- MS14-031: Vulnerability in TCP Protocol Could Allow Denial of Service (2962478) — An attacker could cause a system to stop responding. Microsoft considers it unlikely that successful exploit code could be written.
- MS14-032: Vulnerability in Microsoft Lync Server Could Allow Information Disclosure (2969258) — Lync Server content could potentially execute scripts in the user's browser to obtain information from web sessions. Microsoft considers it unlikely that successful exploit code could be written.
- MS14-033: Vulnerability in Microsoft XML Core Services Could Allow Information Disclosure (2966061) — XML processing could allow an attacker access to more information than is proper. Microsoft considers it unlikely that successful exploit code could be written.
- MS14-034: Vulnerability in Microsoft Word Could Allow Remote Code Execution (2969261) — Word's handling of embedded fonts could be abused to give an attacker remote code execution with the same privileges as the user running Word.
Microsoft also released numerous non-security updates today. The vast majority are for Windows 8 and 8.1, a few for Windows RT and Windows Server 2012 and two for Windows 7 and Windows Server 2008 R2.
A new version of the Microsoft Malicious Software Removal Tool is also available, and runs automatically when users run Windows Update. The new version adds detection and removal for Win32/Necurs, a sophisticated rootkit that puts great effort into combating security software.